mit weniger Risiko.
Content Security Policy (CSP)
Cross-site scripting (XSS) Embedding malicious resources.The Content-Security-Policy header is an improved version of the X-XSS-Protection header and provides an additional layer of security. The web’s security model is based on a same-origin policy.Examples; Content Security Policy (CSP) Examples . Our list includes policy templates for acceptable use policy, data breach response policy, password protection policy and more. Note: frame-src allows you to specify where iframes in a page may be loaded from. The core functionality of CSP can be divided into three areas: Requiring that all scripts are safe and trusted by the .
CSP: report-to
The web’s security model is rooted in the same-origin policy.Receive curated news, vulnerabilities, & security awareness tips.
Content-Security-Policy PHP Examples
com should only have access to https://mybank. Key elements of an AUP may . Content Security Policy (CSP) — 幫你網站列白名單吧.This page outlines Content Security Policy (CSP) as a strategy for reducing the risk and impact of XSS attacks in modern browsers. Always start out with a strict Report-Only policy to map and learn your site. Each component of the CSP header value . A nonce is just a random, single use string value that you add to your Content-Security-Policy header, like so: style-src css-cdn.UPDATED An update to a product from infosec vendor CrowdStrike is bricking computers running Windows. Mozilla Developers Network has .Durch Content-Security-Policy nutzen Sie Firefox und Co.Allow Inline Styles using a Nonce.Examples of Information Security Policies.com; style-src ’self‘ .Content-Security-Policy Examples. It is enabled by .To allow for trusted domain (my-trusty-site.com should certainly never be allowed access. These are free to use and fully customizable to your company’s IT security practices.


It is very powerful header aims to prevent XSS and data injection attacks. In this Stack Overflow question, you can learn how CSP works, how to use it in your web development, and what are the benefits and challenges of implementing it.
Content-Security-Policy
Cross-Site Scripting (XSS) is a security vulnerability where an attacker places one or more malicious client-side scripts into an app’s rendered content.Adopting CSP guides you through this process in more detail, including code examples, and explains how to use tools to help with any necessary refactoring. Each origin is kept isolated from the rest of the web, giving developers a safe sandbox in which to . Access security policy. script-src ’self‘ https://www.A properly configured Content-Security-Policy (CSP) can help prevent cross-site scripting (XSS) attacks by restricting the origins of JavaScript, CSS, and other .On Friday, July 19, 2024, morning, reports surfaced globally of Microsoft Windows operating system users encountering the infamous Blue Screen of Death .
What is Content Security Policy (CSP)
Content Security Policy: how websites are becoming safer. Many developers start out directly setting the Content-Security-Policy http header – . Addresses how users are granted access to applications, data, .You need to generate a random nonce value (using a cryptographically secure random token generator) and include it in the policy.NET Core Blazor apps to help protect against Cross-Site Scripting (XSS) attacks. JavaScript, CSS, ActiveX) can be a security risk for internet users and website operators since they can be manipulated by cross-site scripting.com ’nonce-rAnd0m‘; Assuming our nonce value is rAnd0m (you need to randomly generate a new .com ’s data, and https://evil.A Content Security Policy (CSP) is an added layer of security that helps detect and mitigate certain types of attacks, including: Content/code injection.
CSP: form-action
For example, you can use this key to: Restrict permitted sources for other types .com; object-src ’self‘ EDIT:Examples of security policies. Active content on websites (i. Send a Content-Security-Policy HTTP response header from your web server.Content Security Policy is a mechanism designed to make applications more secure against common web vulnerabilities, particularly cross-site scripting .The HTTP Content-Security-Policy (CSP) form-action directive restricts the URLs which can be used as the target of form submissions from a given context. Security policies come in several forms, including the following: General information security policy.Cross-site scripting.For example, content delivery networks (CDNs) that do not use per-customer URLs, such as ajax. CSP instruct browser to load allowed content to load on the website. If everything is working you should see the following in the HTTP response headers when you make a request to your site:
How to write an information security policy, plus templates
com), do the following: Content-Security-Policy: frame-ancestors my-trusty-site. It aims to prevent activities that may compromise security, violate laws or regulations, or harm productivity. Most pentest vendors are just checking a box to see if exists. Web technology reference for developers.You can use the content_security_policy manifest key to loosen or tighten the default policy. I’ve looked at the official docs, but I still can’t seem to figure out the proper syntax.Project 2025 has been around in some form since early 2023.
Whitelist multiple domains in content security policy
Was steckt hinter dem Sicherheitsstandard für . SANS has developed a set of information security policy templates.configWeitere Ergebnisse anzeigenWhat is Content Security Policy? A Content Security Policy (CSP) is a security standard designed to add an additional layer of security for web applications.CSP: frame-src. Or you can take a look at more CSP examples, if you prefer to learn by example. A nonce is just a random, single use string value that you add to your Content-Security-Policy header, like so: script-src js-cdn. IONOS editorial team 01/11/2023. It is important to note, this nonce value needs to be dynamically generated as it has to be unique for each HTTP request: http. Here a few common scenarios for content security policies: Allow everything but only from the same origin default-src ’self‘; Only Allow .Die Content Security Policy spielt eine entscheidende Rolle bei der Minderung solcher Risiken, indem sie die Quellen einschränkt, aus denen Skripte . See Using Content Security Policy for a general description of CSP syntax. Here’s what you need to know with using jQuery with a Content-Security-Policy HTTP response header or meta tag.Example htaccess file. The following does not seem to work: content_security_policy: script-src ’self‘ https://foo. This key is specified in the same way as the Content-Security-Policy HTTP header.com ’nonce-rAnd0m‘; Assuming our nonce value is rAnd0m (you need to randomly generate a new nonce for every HTTP request), we .I’m looking for a good way to implement a relatively strong Content-Security-Policy header for my ASP. Example CSP Header with . We’ve baked these best practices into the RapidSec product — especially in the Security Manager that help you generate your . Using a hash is one way to allow the execution of inline scripts in a Content Security Policy (CSP).The below 10 tips, learned from years of deploying CSP at scale — will take you from A to Z with regards to proper deployment of Content-Security-Policy without breaking your website / web application. Code from https://mybank.com https://example.By injecting the Content-Security-Policy (CSP) headers from the server, the browser is aware and capable of protecting the user from dynamic calls that will load content into . But in recent months, the Biden campaign has made a concerted effort to raise awareness of Project . Content-Security-Policy: style-src ’nonce-2726c7f26c‘. Firefox 57 doesn’t block the . You could try the following to check the box (warning this does nothing): Content-Security-Policy: . jQuery code that calls the css() function to set the style attribute of an element may be blocked by CSP. It is enabled by setting the Content-Security-Policy HTTP response header.Content Security Policy is a mechanism designed to make applications more secure against common web vulnerabilities, particularly cross-site scripting.
Content Security Policy (CSP) implementation
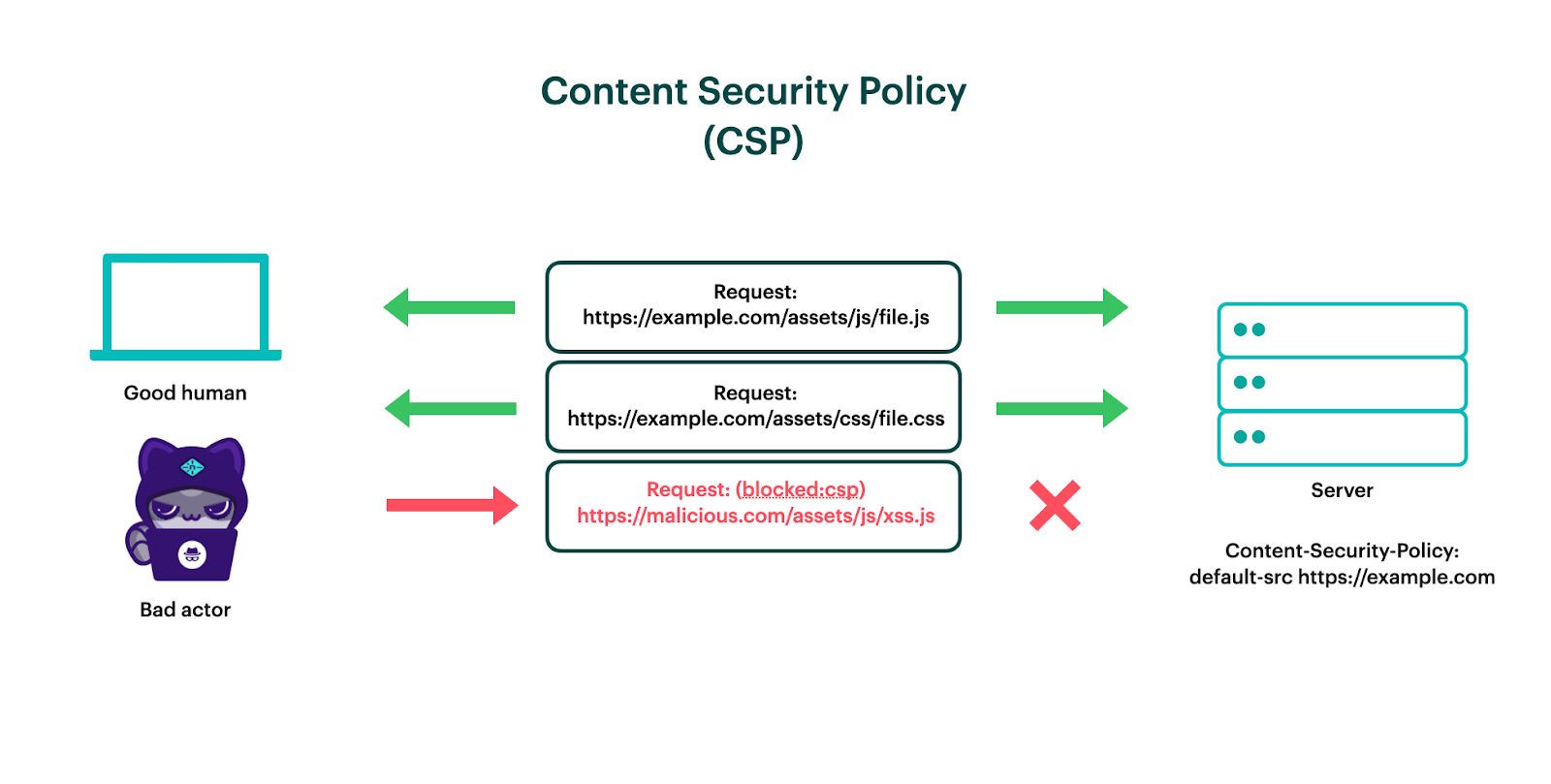
Content Security Policy can significantly reduce the risk and impact of cross-site scripting attacks in modern browsers.This article explains how to use a Content Security Policy (CSP) with ASP.This article contains a collection of different Content-Security-Policy examples. If you compute the SHA-256 hash of our entire JavaScript code block, in our case it is .The global outage impacts a raft of Australian companies and government agencies.Content security policy. You should change such code to use .Content Security Policy. Overview / Web Technology.They are left in there as examples since so many sites include content from those CDNs. Here’s the latest on the company reportedly responsible. Here’s how one might use it with the CSP with JavaScript: Suppose we have the following script on our page: . Content-Security-Policy Header. One last option is to just include a very minimal policy that basically does nothing.Content Security Policy (CSP) is currently supported in model-driven and canvas Power Apps. Let’s suppose we want to add a CSP policy to our site using the following: Header add Content-Security-Policy default-src ’self‘; Your policy will go inside the double quotes in the example above. The Content Security Policy (CSP) was introduced .CSP Hash Example.
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-03.jpg)

This differs from frame-ancestors, which allows you to specify what . Warning: Whether form-action should block redirects after a form submission is debated and browser implementations of this aspect are inconsistent (e. All major browsers currently offer full or partial support for . Here’s how to add a Content-Security-Policy HTTP response header using Java. Content security policy. Using a header is the preferred way and supports the full CSP feature set.com, should not be trusted, because third parties can get content onto their domains. References References. Malicious iframes (clickjacking) To learn more about configuring a CSP in general, refer to the Mozilla documentation . [CSRF] One click attack: 利用網站對使用者瀏覽器信任達成攻擊. Send it in all HTTP responses, not just the index page.Manieendar Mohan.Content-Security-Policy: default-src ’self‘ What goes inside a CSP policy? If you’re not sure what default-src ’self‘; means, then check out the Content Security Policy reference for details. We’ll include common directives for you to mix and match along with security .NET WebForms application.Geschätzte Lesezeit: 7 min
Content Security Policy
The Content-Security-Policy HTTP header provides fine-grained control over the locations from which resources on a site can be loaded. Content-Security-Policy: .The HTTP Content-Security-Policy-Report-Only response header allows web developers to experiment with policies by monitoring (but not enforcing) their effects.com must have access to only https://mybank.Content-Security-Policy Java Examples.

These violation reports consist of JSON documents sent via an HTTP POST request to the specified URI defined in a Reporting-Endpoints HTTP response header. Skip to main content ; Skip to search; Skip to select language; Open main menu.The Content-Security-Policy Report-To HTTP response header field instructs the user agent to store reporting endpoints for an origin. For example, code from https://mybank. CSP Java Example. In addition to whitelisting specific domains, content security policy also provides two other ways of specifying trusted resources: nonces and hashes:
Content-Security-Policy with jQuery
In a rarity for an in-the-weeds policy memo, Project 2025 has made its way into the wider public, drawing condemnations on late-night shows, podcasts and awards . Admins can control whether the CSP header is sent and, to an extent, what it contains. Components of CSP. One of the easiest ways to allow style tags when using CSP is to use a nonce. Content Security Policy (CSP) is a security header that assists in identifying and mitigating .
Config your IIS server to use the Content-Security-Policy header
Overview
Content-Security-Policy (CSP) Header Quick Reference
javascript – How does Content Security Policy (CSP) work . 雖然瀏覽器有 同源政策的保護 (Same .The HTTP Content-Security-Policy response header allows website administrators to control resources the user agent is allowed to load for a given page.Content-Security-Policy Spring SecurityHow to add Report-To Content-Security-Policy directly in web.One of the easiest ways to allow inline scripts when using CSP is to use a nonce. Acceptable Use Policy (AUP) The AUP sets the ground rules for using an organization’s IT resources, including computers, mobile devices, networks, email systems, and the internet. jQuery css() function. The settings are at the environment level, which means it would be applied to all apps in the environment once turned on. Another Option for PHP In this section, we’ll explain what content security policy is, and describe how CSP can be used to mitigate against some common . The HTTP Content-Security-Policy (CSP) frame-src directive specifies valid sources for nested browsing contexts loading using elements such as and