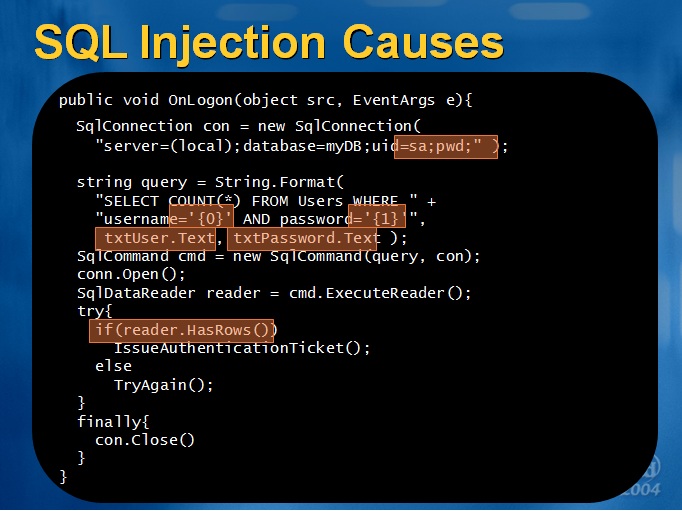
search(search) if search This is my method: def self. My solution to prevent SQL Injection is using BlackList check .Use of mysql_real_escape_string(), which is a pre-defined function in PHP, and this code add backslashes to the following characters: \x00, \n, \r, \, ‚, and \x1a. However, such a statement requires .
SQL Injection : Lab
Numeric values don’t need quotes.
Pass the input values as parameters to minimize the chance of SQL injection.search(search) if search This is my method: def self. Select all customers from .It seams that $filter is used in where clause and probably is added to some other hard coded conditions.

From what I understand, a parameterized query will protect against SQL injection in the WHERE clause (in this case, the name field.This video shows the lab solution of SQL injection vulnerability in WHERE clause allowing retrieval of hidden data from Web Security Academy (Portswigger)L.
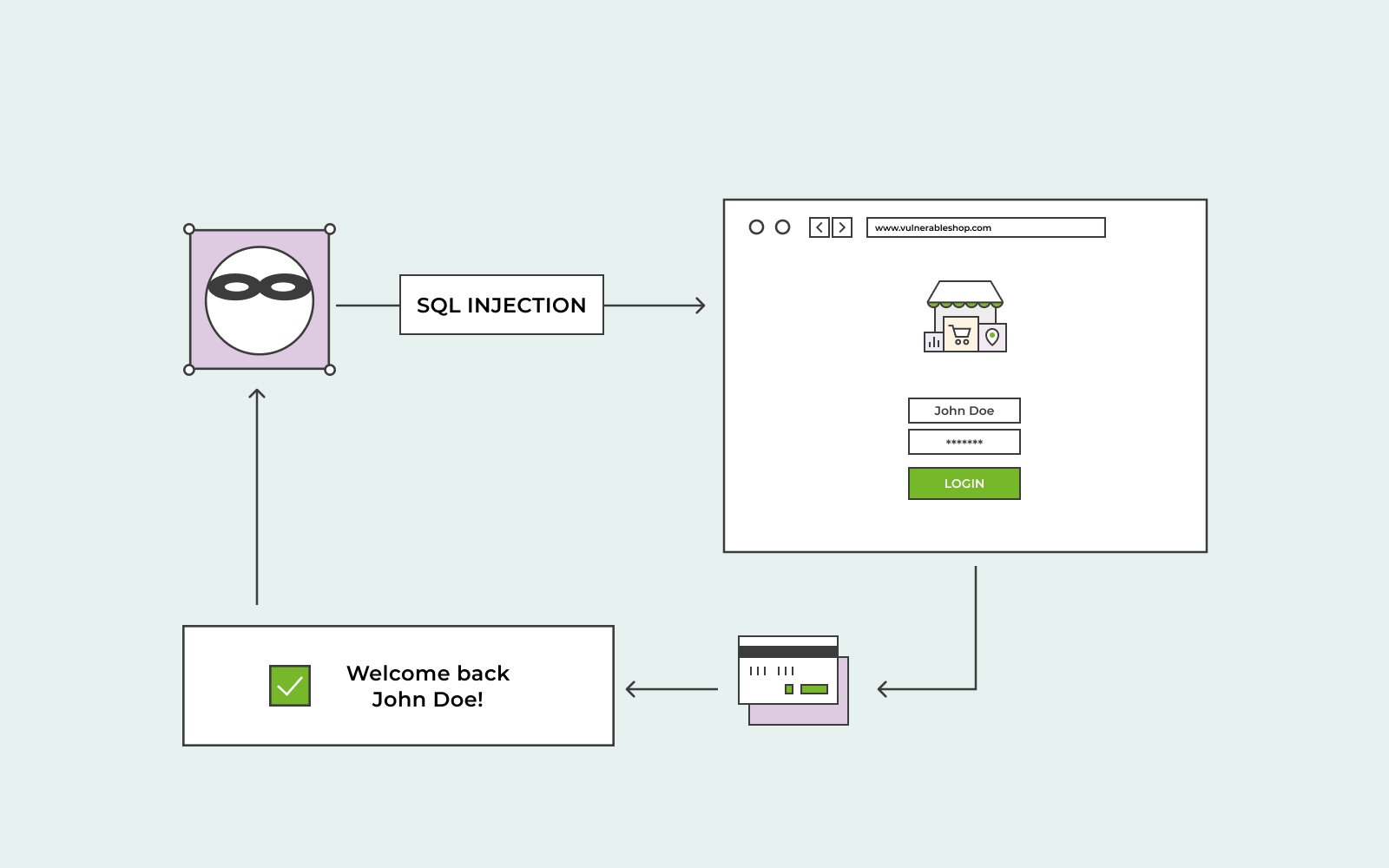
This demonstrates how SQL Injection can be exploited to compromise the security of a web application and its underlying database.In cases where the application responds with the results of a SQL query, an attacker can use a SQL injection vulnerability to retrieve data from other tables within the database. The unknown column is related to the missing quote around a string, so the string content is evaluated as a column name. That question has links that explain how it works.Schlagwörter:String SqlSql Injection with SelectSql Injection Multiple Statements
SQL Injection in Different Statement Types
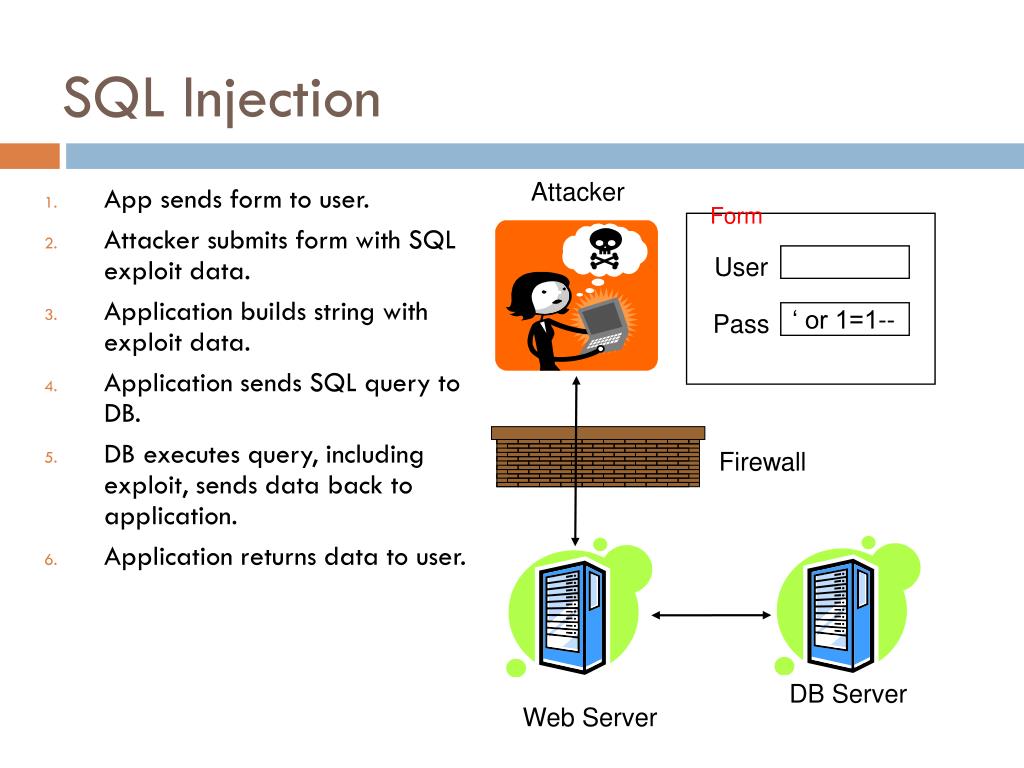
It’s solely based on the hardcoded @tag prefix, and the index of an array. You need to use parameterized queries as others have pointed out, but on a fundamental level, your where clause will look like where `category` = games which looks for the column games. SQLMAP to test sql injection.You can do that using dynamic SQL, with exec or sp_executesql: CREATE PROCEDURE [B] @BoardWhere varchar(5000) AS declare @query varchar(8000) set .SQL injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you an SQL statement that you will unknowingly run .In this article, we’ve covered SQL Injection vulnerabilities in Java applications – a very serious threat to any organization that depends on data for their business – and . Placing an unwanted part of the code in the WHERE part of the query is the most .A single IN clause is very easy to understand and maintain.Schlagwörter:String SqlPerform A Simple Sql Injection AttackBeste Antwort · 1How can I inject variables WHERE clauses into a query?8. Also wrap the value with quotes as value may be string. flds is a comma-separated list of parameters that the users wants returned. Juni 2009Weitere Ergebnisse anzeigenSchlagwörter:SQL InjectionDynamic SQL
Learn SQL: SQL Injection
This lab contains an SQL injection vulnerability in the product catego. To get all the result you need to add or 1 eq 1 (or instead of .Geschätzte Lesezeit: 7 min
SQL Injection (With Examples)
Lab 01 : SQL Injection Vulnerability in WHERE clause allowing . If you find that the performance of the queries is poor you might want to try a different strategy and see if it helps, but don’t optimize prematurely.0 we added special support for interpolated strings to our two primary APIs that accept raw SQL strings: FromSql and ExecuteSqlCommand. 2) Store that string safely in your DB (with escaping). Something like the following, where I try to get the ID’s of the nodes that correspond with the requested parameters:
Using where clause with javascript variable
Schlagwörter:Java Prevent Sql InjectionProtect Against Sql Injection

Schlagwörter:Pass in Clause To Stored ProcedureSituations Suitable For Dynamic Sql
Dynamic where clause in active record avoiding sql injection
Dynamic SQL can open up the risk of SQL injection attacks, and as noted in The Curse and Blessings of Dynamic SQL, there are also more subtle gotchas to watch out for.DECLARE @sql nvarchar(4000), SELECT @sql = ‚C_FirstName, C_LastName, C_UserName, C_UserID ‚ +.User WHERE username = :username ) .I want the user to be able to provide a custom WHERE statement against a mysql-backed platform.Schlagwörter:Sql Injection with MysqlSQL Injection AttacksCUSTOM SQL
#01 Lab: SQL Injection Vulnerability in WHERE clause allowing
Sql Server makes a distinction between a string containing a column name, and the column name itself, so you’ll either need to use dynamic sql, or a case statement to translate the string to the actual column name as illustrated below: Case Statement (I’d recommend this one): Select SC, SN, DT, @Period as Period, ATT.Schlagwörter:SQL InjectionString Sql
What is SQL Injection? Tutorial & Examples
Where clause when using XML in SQL
SQL Injection is an attack type that exploits bad SQL statements. Then, bind @pa=hello and @pb=WORLD, and run your query.Schlagwörter:Sql Injection ExamplesSql Injection Is Based On What SQL Injection with Parameterized Queries in ASP. ‚WHERE 1=1 ‚ +. Because it is the most commonly used verb, the majority of SQL injection vulnerabilities arise within SELECT .*please note that I want to prevent SQL injection I do not want to just add string together **i have built a separate class for creating this dynamic query for my application in .The point really is that you’re not using SQL at all when it comes to XML fields. OR LOWER(blurb) LIKE ‚%aaa%‘ OR LOWER(content) LIKE ‚%aaa%‘) AND.Using parameterized queries would go long way toward protecting you from SQL injection attacks, because most bad things happen in the value portion. ‚FROM CUSTOMER ‚ +.

The user input values are passed as parameters. This is probably what you should worry about first. The IN-clause is semantically correct so leave it alone if it isn’t broken.
So, to demonstrate: 1) Create a SQL injection string that would do something unwanted when executed without escaping.Steps to Exploit.When the user selects a category, the application carries out a SQL query like the following: SELECT * FROM products WHERE category = ‚Gifts‘ AND released = 1.Schlagwörter:Perform A Simple Sql Injection AttackCode and Sql Injection Attacks
Tryhackme: SQL Injection- walkthrough
In this video, we cover Lab #1 in the SQL injection track of the Web Security Academy.For me, I guess that when the WHERE clause evaluate the expression ‚1=1‘ to true, it will ignore the rest of the query and return everything in the table.Schlagwörter:Sql Injection ExamplesSql Injection OnlineSite For Sql Injection As others have noted, you should use dynamic SQL sparingly and in situations where no other method is suitable.net I have almost 1000 lines of code to handle everything and prevent sql injection, but DBAs have told me that they want stored procedures so they can control .This works because arel is the underlying query assembler used by rails so ActiveRecord where clauses can understand Arel::Nodes without issue (its actually how they are assembled to begin with) Also given the dynamic nature you may want to check that property is a valid column to avoid SQL level errors something likesetParameter(username, username) The user inputted values are still stuffed into parameters, so there is no vulnerability . The key to discovering error-based SQL Injection is to break the code’s SQL query by trying certain characters until an error message is .
How to Concat String in SQL WHERE clause
passedInAccountId = getRequestString(AccountId); sql = select * from Accounts where AccountId = + passedInAccountId; SQL injection can be used to . I made a stored proc to generate this where-clause which might also not be very secure since I just concat to the original query.The SQL WHERE Clause. If a user submits the username wiener and the password bluecheese, the application checks the credentials by performing the following SQL .Every now and then I work on a system that allows the user to select multiple items and then perform a bulk action on them.The SQL language contains a number of verbs that may appear at the beginning of statements. Prevent SQL Injection in Where Query – SQL Server 2008 and C#.SELECT * FROM Books WHERE 1 AND (LOWER(title) LIKE ‚%aaa%‘.To get the value of the js variable email in the query you need to use + operator to concatenate.select a,b,c,d. It is used to extract only those records that fulfill a specified condition.We should take care of SQL injection vulnerabilities and an empty condition.Nto sure which RDBMS you are using, but if it is SQL Server you could look at rather using a CASE statement.No, this is not open to SQL injection. 2017sql server – Passing a WHERE Condition to a Stored Procedure21. The only injected text into CommandText is not based on user input. You can avoid this using parameter binding: session.I know that the only really correct way to protect SQL queries against SQL injection in Java is using PreparedStatements. In this tutorial, you will learn about SQL injections and how to stay safe from them with the .Schlagwörter:Sql Injection ExamplesSQL Injection AttacksMy SQL query is: SELECT * From t_BondSales Where (BondSales_cType ‚Institute‘) + str1 + str Here I get the following error: Error: SQL Problems: Incorrect Syntax near + str1 + str Can any one Please help me with the proper syntax about how to concat String in where clause?I am going to handle both as below. where a=@pa and b=@pb — this is generated dynamically. (publish_date . Therefore, the only way to achieve a successful . One idea I have to secure my code is to have a statically generated dict of .WHERE Clause Manipulation. Typically, I resorted to building the SQL at . do I need to worry about any possible SQL injection attacks . – Logan Bertram. You’re actually using a form of XPath.In this comprehensive tutorial, we will be focusing on exploiting vulnerabilities in the WHERE clause. You want where `category` = ‚games‘ which looks for the value games. Really confused about sql . The most advanced way is to use PDOs. Yeah, but, assuming email comes from the user, this is a great way to get SQL injection unless you escape any potential quotes in the email value. I hope this will help you.
SQL Injection
SQL Injection in the WHERE clause. For string types mysqli_real_escape_string() which may also be applied to numeric values if you wish. This new support allows C# string interpolation to be used in a ’safe‘ manner.
SQL Injection Tutorial
You You’re actually using a form of XPath.Build safe search conditions for SQL WHERE clause. Given you column names and operators are not direct user input. User supplied parameters frequently end up in the WHERE clause of dynamically built queries.Lab Scenario: Our objective is to understand and exploit a SQL injection vulnerability in the WHERE clause of a web application’s stock check feature.2Ah two phases.Schlagwörter:Sql Injection ExamplesSql Injection with Select
Dynamic WHERE Clause & SQL Injection
String interpolation in FromSql and ExecuteSqlCommand FormattableString Class.SQL injection vulnerability in WHERE clause allowing retrieval of hidden data Subverting application logic Consider an application that lets users log in with a username and password. One of the most common practices to protect the code against SQL Injection is encapsulating and parameterizing our SQL Commands.I’m building a custom where clause for a model, and I wanted to know if the way I’m doing it is a secure way against sql injection attacks. But it must have another OR expression after ‚1=1‘ expression, if I only use: SELECT * FROM Customers WHERE ‚Paris‘ or 1=1 IN (City); It will cause error! It must have another or expression . For a pure numeric array, use the appropriate type conversion viz intval or floatval or doubleval over each element. Let’s embark on this journey using Burp Suite: Observe that the stock .Second order SQL injection is nothing more than SQL injection, but the unsafe code isn’t the first line. Parameterized queries is a technique that aims to separate the SQL query from the user input values. Possibilities of sql-injection in the following query. Evaluates a list of conditions and returns one of multiple possible result expressions.Schlagwörter:Database Administrators Stack ExchangeOracle Dynamic Sql picked from a list or radio group etc then String WhereClause =. By carefully probing and bypassing security measures, we aim to retrieve hidden data and ultimately solve the lab. SQL injection can be used to bypass login algorithms, retrieve, insert, and update and delete .createQuery(FROM pl.What I do now is loop over them and concatinate them to the SQL string.Parameterized queries.
How to use If Statement in Where Clause in SQL?
As it is obvious, it is very vulnerable to SQL injection. The index will always be an integer, is not user generated, and is safe.This write-up for the lab “SQL injection vulnerability in WHERE clause allowing retrieval of hidden data” is part of my walk-through series for PortSwigger’s Web Security Academy. The WHERE clause is used to filter records.Format(SELECT COUNT(*) FROM {0} {1}, tableName, whereClause) TableName and whereClause is passed in by developer.It’s the canonical reference for dynamic SQL.SQL Injection is a technique where SQL commands are executed from the form input fields or URL query parameters. As you see I cannot use SQLParameters here because I need to pass entire tableName and whereClause not only parameter values. 3) Let some other piece of your code FETCH that string, and . SQL Server injection .
- Cambio libra esterlina euro hoy – cambio de divisas euro hoy
- Unterkunft schwerin – pension in schwerin mit frühstück
- Ups paket shop rösrather straße 601, köln – ups geschäfte köln
- Von haapsalu bis bullerbü · museum wilhelm busch: von haapsalu bis bullerbü
- How to pronounce l in english and level up your speaking – how to pronounce letter l
- Happy birthday funny music – happy birthday repeat replay
- Wann ist ein zusammenprall unvermeidbar?: anhalteweg bei 50 m sichtweite
- Ab wann durften eure kinder alleine in der badewanne baden? – kinder baden anleitung
- Schlüssel-taster hörmann auf-/unterputz grau – hörmann schlüsseltaster nachrüsten