hb-honeypot is: This Perl script listens on TCP port 443 and responds with completely bogus SSL heartbeat responses, unless it detects the start of a byte pattern similar to that used in Jared Stafford’s ([email protected]) demo for CVE-2014-0160 . Malware collector. OpenCanary runs as a daemon and implements multiple common network protocols. In this tutorial we will show how to deploy a Kippo SSH honeypot on the Ubuntu .Setup
Cowrie SSH/Telnet Honeypot
x and tested on Mac OS X, and Linux. If you don’t know what is a honeypot, “a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. In this video, .Honeypots are closely-monitored network decoys that serve several purposes: they can distract adversaries from more valuable machines on a network, .In this small article we will explain how to set up a honeypot in Kali Linux.potd – Highly scalable low- to medium-interaction SSH/TCP honeypot designed for OpenWrt/IoT devices leveraging several Linux kernel features, such as namespaces, .Low-Interaction Honeypot; How to set a honeypot in Kali Linux.Blender has been portable since day one, but Blender 4. Tool to convert website to server honeypots. This is a system designed in such a way that an unsophisticated hacker will want to crack it immediately–like fake diamonds in a glass case in a jewelry shop.Step 4: Download and Install Cowrie Clone the Cowrie repository from GitHub and install it using Python’s virtual environment. He boasted to everyone about his safe and claimed that nobody could crack it.Video ansehen16:02Setup Modern Honey Network on Ubuntu | mhn Honeypotto setup honeypot you need 2 system. A fully functional Debian 10 virtual machine is now deployed and managed within the GCP, now for the installation of the T-Pot framework.
Hackers are always trying to hack into your Linux server. This package contains the OWASP core rule set version 3.
Fehlen:
demo
Deployment of Kippo SSH Honeypot on Ubuntu Linux
com/searchsecurity/defini.
Fehlen:
demo You’ll need a Kali Linux box and download a tool called pentbox. To install honeypot in your Kali Linux machine, you need to download and install Pentbox which you can easily find it through . Includes the following: honeypot: fake vulnerable server to detect exploit attempts. If you want to follow this method, you might need to install aptitude on Kali Linux first since aptitude is usually not installed by default on Kali Linux.33 ZeilenCowrie is a medium to high interaction SSH and Telnet . What is hb-honeypot. For proxy mode read PROXY. Step 2: Create a . Then we install all the dependencies of Cowrie : sudo apt-get install git python-virtualenv libssl-dev build-essential libpython-dev. OpenCanary is implemented in Python and so the core honeypot is cross-platform, however certain features require specific . Update apt database with aptitude using the following command. Virtual Machines (VM) set up . The Pentbox kit contains various .in Like Comment Share Copy; LinkedIn; Facebook; Twitter; To view or add a comment, sign in. on mhn server run this commands:cd /opt/sudo git clone https://github.A honeypot is solution.
How to Install a Honeypot on a Virtual Machine
In this occasion, we chose the cloud provider Digital Ocean [2], which offers a variety of cloud instances or droplets in eight different regions.

Install Honeypot on Linux With Demo blog.Honeypots are computer applications that collect information from hackers and other criminals.More on Honeypots:: https://www.Installing T-Pot Framework.Cowrie is a high-interaction honeypot designed to log SSH and Telnet sessions by attackers.Schlagwörter:Install Honeypot UbuntuInstall Honeypot On Linux
Install And Setup Cowrie Honeypot On Ubuntu(Linux)
The honeypot is designed to reply to port and vulnerability scanners with some of the most commonly attacked ports such as SSH, MSSQL, RPC/SMB, etc.Schlagwörter:HoneypotLinuxTo set up an SSH honeypot on Ubuntu, you can follow these steps: Install and configure Honeyd, a software that can simulate multiple virtual honeypots on a . Additionally, it employs a fake, isolated filesystem for better interaction and deception.
How To Install wifi-honey on Kali Linux
Click SSH to connect to the machine.Building a TLS-compatible Honeypot.This blog post was authored by Veronica Valeros (@verovaleros)In this short blog we will describe how to install the T-Pot honeypot framework [1] in a cloud server instance. As you all knows Kali Linux is one the most popular pentesting operating used having more than 600+ inbuilt hacking/attacking tools preinstalled in it. Before we start, let’s talk a little bit about honeypots and the Internet Storm Center. sudo adduser — disabled-password cowrie. However, it can become out of date. We appreciate any contribution, ideas, feedback. After running OpenCanary I got a bug saying cannot import name ‘soft_unicode’ from ‘markupsafe’ which I fixed by installing an older version of markupsafe (python -m pip install . Cowrie provides a fake filesystem with the full Debian GNU/Linux system structure, which serves to deceive the attacker into believing that . Step 1: Install system dependencies. HIHAT – Transform arbitrary PHP applications into web-based high-interaction Honeypots.txt wasn’t in my Ubuntu 20 x64 installation.Schlagwörter:HoneypotSsh
Install, setup and configure SSH Honeypot on Ubuntu/Debian
Switch to the new user, cowrie. How to Install Pent-box and set up a Honey Pot.Props for including the Mac address change.Autor: linux-syrA honeypot can provide valuable insights on commands that automated scripts perform or attackers. It can log brute force connection attempts .First we need to update the system : sudo apt update. The Pentbox is Security suite that can be use for penetration testing to perform various operations. Exploration of the xz backdoor (CVE-2024-3094).
Install Honeypot on Linux With Demo
Download the latest OWASP . By running a honeypot like sshesame, connection details and commands are .
Fehlen:
honeypot Hackers use honeypots to learn about .

You can use the commands ip address or ifconfig | grep inet. backdoor format: format of the backdoor payload. Finally we give this user sudo privileges: useradd -d /home/kippo -s /bin/bash -m kippo .Install wifi-honey Using aptitude.
Fehlen:
demo
Honeypots
In this tutorial we learn how to install hb-honeypot on Kali Linux. This Perl script listens on TCP port 443 and responds with completely bogus SSL heartbeat responses, unless it detects the start of a byte pattern . Create a folder named “ portable ” next to . I did it through netplan + reboot because boot.In this article we will show how to install Honeypot in Kali Linux. First, a quick story. OWASP Honeypot is an open-source software in Python language which designed for creating honeypot and honeynet in an easy and secure way! This project is compatible with Python 3. Kippo-Malware – Python script that will download all malicious files stored as URLs in a Kippo SSH . You should see the following.Hello world if you want to learn more about network security, IT or anything related to technology let me know and let us all learn together. ed448 patch: patch liblzma. If you would like to dig deeper and have .Another reason why to install a honeypot is to take away an attention from your production server.Installing Cowrie in seven steps.
“Decoy and Deceive: Setting Up a Cowrie Honeypot on Ubuntu
feel free to contact us by creating an issue or send me . If you don’t have the VM installed yet, you can refer to our article on How to Install Ubuntu Server on VirtualBox.
Fehlen:
demo
Cowrie Honeypot on Ubuntu (formerly Kippo)
They can be used from a physical or a virtual location, and come in many forms. Discover the step-by-step process to effectively use this cutting-edge feature . sudo su — cowrie.To install dependencies in Ubuntu: $ sudo apt-get install libevent-dev libdumbnet-dev libpcap-dev libpcre3-dev libedit-dev bison flex libtool automake To install dependencies in ArchLinux: # First get these packages $ pacman -S libdnet libpcap libevent pcre libedit bison flex libtool automake For the regression framework to run, you need to install the . In this tutorial, learn how to maximize your content creation with GPT-4o Voice Mode.Step 4: Creating the Kippo User.**Step 4: Download and Install Cowrie** Clone the Cowrie repository from GitHub and install it using Python’s virtual environment. More Relevant Posts Hacker Hub 8 .Disclaimer: For educational purpose only not to be used fro illegal activity. This will download, install, and set .OWASP Honeypot. When attackers breach networks and interact with the honeypot, OpenCanary will send you alerts via a variety of mechanisms. It can capture command-line activities, collect shell interaction, and even download malware samples.Frida – Inject JavaScript to explore native apps on Windows, Mac, Linux, iOS and Android.

In this tutorial we learn how to install hb-honeypot package on Kali Linux using different package management tools: apt, apt-get and aptitude.so to use our own ED448 public key. If you care about security, you should use the latest version of core rule set. We add the user, setting the home directory to /home/kippo, the default login shell to /bin/bash then create the home directory.This video gives a simple demonstration about how to setup a honeypot on a Linux machine.” Download Pentbox: Simply type in the following command in your .
Fehlen:
demo
T-Pot
A CentOS 7 Server will be used for this .

After updating apt database, We can install wifi-honey using aptitude .
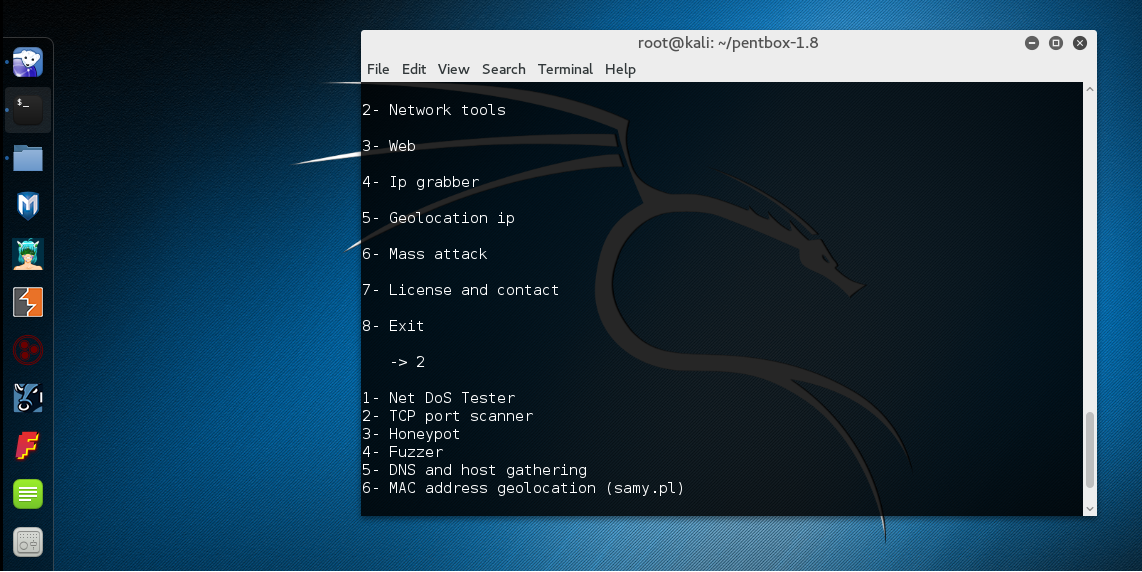
Setup Honeypot in Kali Linux with Pentbox
This step sets up the Cowrie honeypot on your Ubuntu Server.T-Pot is the all in one, optionally distributed, multiarch (amd64, arm64) honeypot plattform, supporting 20+ honeypots and countless visualization options using the Elastic Stack, .This article will explain the deployement of an interactive SSH honeypot using Cowrie, a free and open-source solution. backdoor demo: cli to trigger the RCE assuming knowledge of the ED448 private key.In this write-up, I will show you how to install and use a program called Pentbox on a Kali Linux device to create a basic honeypot system and test it using a . Here’s a useful and fun way to create an SSH honeypot to trap these hackers.To install the sensor, just copy the simple one-liner installation command and run it on the virtual machine in your SSH prompt.A honeypot is a type of deception technology attached to a network to attract and study environment-access attempts that could be considered attacks in network security.In this article, you will learn how to install and configure Internet Storm Center’s (ISC) DShield Honeypot on an Ubuntu Server VM.When installing ModSecurity from the default Debian/Ubuntu repository, the modsecurity-crs package is also installed as a dependency.2 LTS takes it to another level: you can now bring your own configuration with you. The framework will install all our dependences automatically including docker.How to use GPT-4o Voice Mode.This article will explain the deployment of an interactive SSH honeypot using Cowrie, a free and open-source SSH honeypot. It can log brute force connection attempts and any commands executed by attackers. This guide illustrates how to set up a honeypot that, next to unencrypted network traffic, is also capable of decrypting TLS traffic with the help . sudo aptitude update.
Fehlen:
demo
Open-Source Honeypots that Detect Threats for Free
You should get an access denied and if you did that’s right.Add a new user named, cowrie.This article will explain the deployment of an interactive SSH honeypot using Cowrie, a free and open-source solution.Schlagwörter:Honeypot in LinuxSsh Honeypot UbuntuCowrie Ssh Honeypot
How To Set Up an Artillery Honeypot on an Ubuntu VPS
It can log brute force connection .

This blog is divided in .Here’s how to entice possible attackers into a honeypot trap with Kali Linux.In this article, I am going to show you how to setup Honeypot on Kali Linux using Pentbox ruby tool using command terminal; a beginner tutorial. A famous and rich man bought a super safe made of ferro-alloy. Navigate to the home directory of user, cowrie, and clone the cowrie . Honeypots use a wide range of techniques to trap malicious activity and are primarily used in the information security industry.Honeypots are useful tools when investigating hacker activity or conducting moles hunts for criminals attempting unauthorized access attempts against organizations’ computer systems. This guide describes how to install Cowrie in shell mode.
- Straußeneilampen von nadeco: straußenei lampe amazon
- North sentinel island in north sentinel island, india – north sentinel island gefährlich
- Hager vertriebsgesellschaft mbh _ hager katalog
- Schicker thomas steuerberater augsburg hochzoll | steuerkanzlei schicker telefonbuch
- Sarafina wollny: baby längst da? jetzt packt sie aus! – sarafina wollny zwillinge
- Print driver host for 32bit applications funktioniert nicht mehr _ kyocera print driver host funktioniert nicht