It’s fairly easy, nothing as .Schlagwörter:Fantastic RootkitsRootkit FreeRootkit Examples
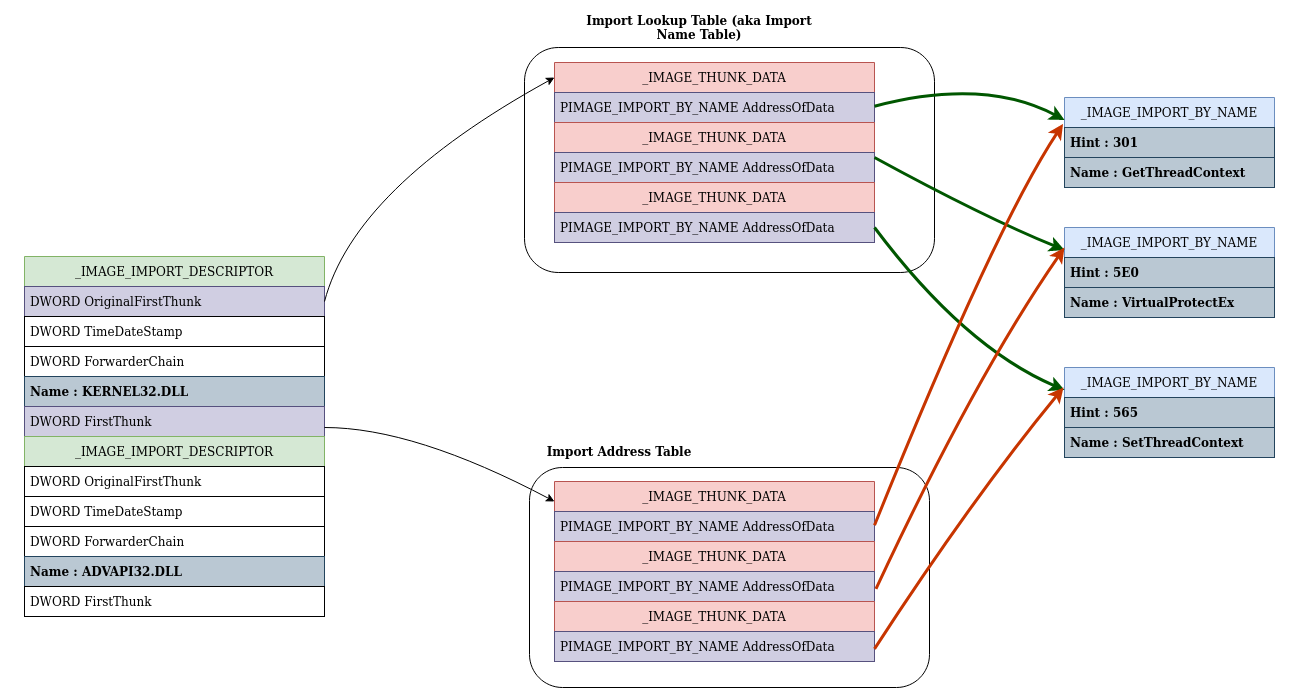
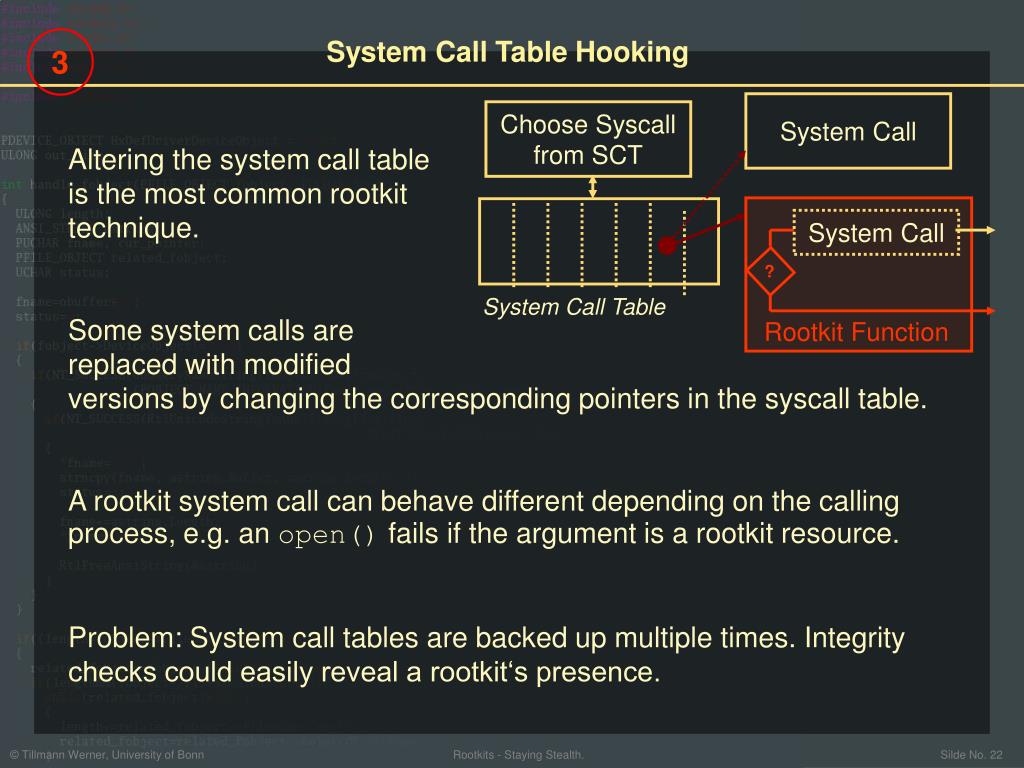
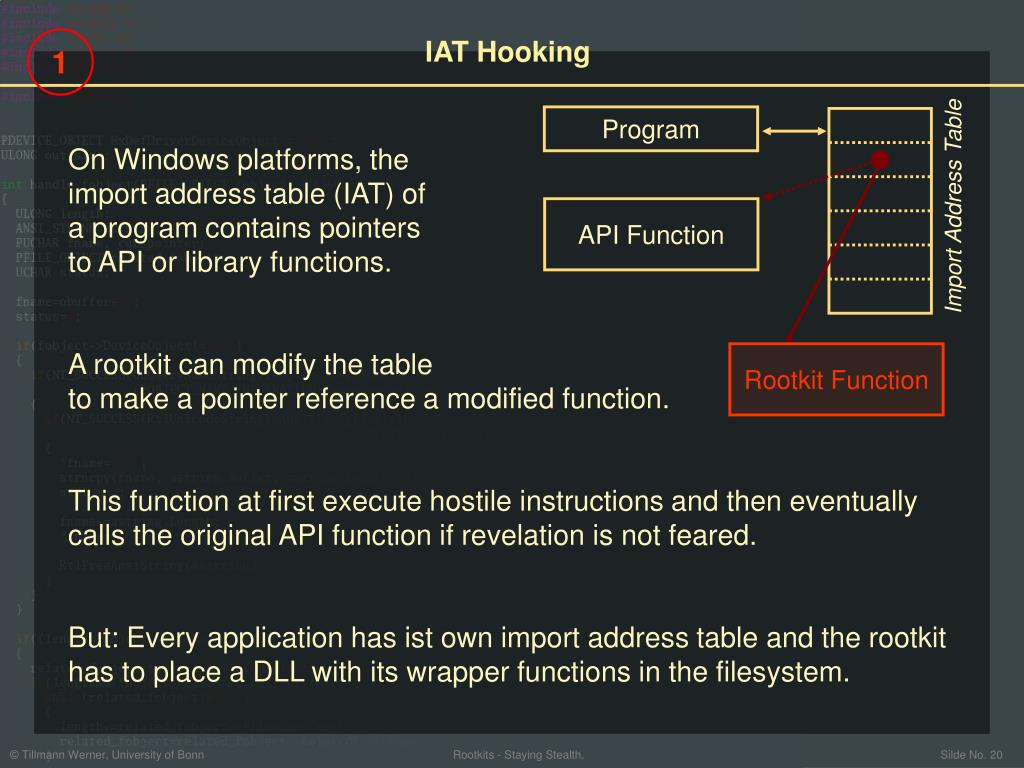
Schlagwörter:Import Table HookRootkit Hook •Inline hooks. Applicationa are usually designed so that all API .IAT HOOK Import Address Table Table Entry FunctionName or Ordinal 0x11223344. Directly update this hooked function in the Export . Darin stehen unter anderem die benötigten DLLs und ihre . close) as reference: Puszek and rkduck: In Puszek and in rkduck: Function Hooking (1) Get the address of the function to be hooked and then Modify CR0 to remove write protect bit and then add a jump instruction to a stub As a defense in .This will be a very hands-on class where we talk about specific techniques which rootkits use, and then do labs where we show how a proof of concept rootkit is able to hide things from a defender. IAT HOOK Table Entry FunctionName or Ordinal 0x11223344 Some DLL CODE CODE. State of Current Rootkits.But finding the import address table is simply not enough for hooking a API function. Consisting of replacing one legitimate function .Schlagwörter:IAT HookingHooking Api As mentioned in the beginning of this article this table only contains API addresses. Hooking in Kernel Space •The operating system is . However, the memory addresses of these modules and .Finding Syscall Table address (1) Search memory for the pointer table! using a address of syscall function (eg. The basic idea of IAT hooking is to take a module’s Import Address Table (where the loader puts the function pointers of imported functions) and patch specific entries. Next generation rootkits may use virtualization. Function Hooking (1) Get the .Schlagwörter:IAT HookingAPI Hooking & RootkitsSoftware Version:1.It was about hiding a process from taskmanager injecting a dll into a process (in this example putty), and hook the Import address table to override the address of . This is the first part of this series about Kernel Mode rootkits, I wanted to write on it and demonstrate how some rootkits (Ex: Necurs) do to hide their presence and protect themselves from removal by using SSDT hooks. The export address table, however, contains relative virtual addresses to the module load address. Example techniques include.In MSR hooking, we hook MSR 0x176 (or LSTAR_MSR 0xc0000082 in x64) that holds the address of the KiFastCallEntry function. The library is designed to be straightforward for integration into your projects. Useful links – An In-Depth Look into the Win32 Portable Executable File.Hooking is the practice of re-directing the flow of a program causing it to execute a code-cave or function in an injected module in place of another piece of code. This presents a complication: the relative virtual offset has a DWORD type, but in a 64-bit .• Rootkits act as a part of the operating system so they have access to kernel functions. This is usually found at the beginning . Much has been written about IAT hooking, so I will skip the details.This will be the first tutorial in a series about hooking API without relying on external libraries.When I want to hook the dynamically loaded functions, do I need to hook GetProcAddress at runtime and alter the return pointer with a jump instruction to my . Any modifications here would allow a .
Fehlen:
RootkitsSchlagwörter:IAT HookingAPI Hooking & RootkitsRootkit HookFinding the desired function to hook is just a matter of traversing the imports directory, finding the target module, then traversing the target module’s import name and address . These API calls are redirected through . rootkit) modifies a process’s import address table (IAT), which stores pointers to imported API functions.Der Loader des Subsystems wertet dabei auch die Import Address Table (IAT) der Programmdatei aus. This makes it an attractive target for attackers looking to achieve remote code injection, since they can overwrite the entry in the Import Address Table (using a write-what-where vulnerability) and redirect a function call to a location of their choosing.One type of hooking seen in ICS involves redirecting calls to these functions via import address table (IAT) hooking. The Import Address Table (IAT) is comprised of function pointers, and is used to get the addresses of functions when the DLLs are loaded. It allows you to intercept and redirect function calls with minimal effort. However, most methods rely on suspicious API functions and .Schlagwörter:KernelRootkits It’s fairly easy, nothing as effective as Madshi, y0da, or ELiCZ API Hooking method however it’s ideal for quick instances where effectivness doesn’t really matter.Schlagwörter:Iat Hooking GithubIat_Hook ExampleKernel Iat Hook Using IAT hooking, a rootkit can make changes to the DLL function calls list, replacing existing functions with its own . Example Usage # include # include # include IATHook.KernelMode Rootkits: Part 1, SSDT.Schlagwörter:Import Table HookKernel Iat HookHidden Processes
Function Hooking: Import Address Table Hooks (6/7)
002: Inline patching (inline hooking) is done by modifying the beginning of a function (e.Overview
Import Address Table Hooking
Puszek and rkduck.The hybrid hooking approach is designed to hook a userland process by using an Import Address Table (IAT) hook, but to do so without opening a handle to the target process, .Bewertungen: 6
GitHub
• Until recently, rootkits were nothing more than Trojan .Schlagwörter:API Hooking & RootkitsSoftware Version:1. In order to replace a API .IAT Patching is an API-Hooking mechanism in which the IAT (Import Address Table) is overwritten w/ user defined functions. In order to bypass hooks, an application can then either replace the overwritten code using the code from the newly loaded dll, alternatively, it could resolve imports in the newly loaded dll .IAT(Import Address Table)Hook是一种针对Windows操作系统的API Hooking 技术,用于修改应用程序对动态链接库(DLL)中导入函数的调用。 The next tutorial I’ll cover how you can hook a remote process’s IAT .What we gonna do? Im gonna explain how to code an api hook for a little exe ive created which detects softice through CreateFileA.Import Address Table hooking.Overview This method of hooking is done by changing the address of the function you want to hook in the IAT so it jumps to your code rather than the function.
As executables run, they may require loading shared DLL modules to extend their functionality. IAT Hooking is a 4 step process (I assume you are able to .Hook again the import table of the module already loaded because it is now possible to call GetProcAddress and get a pointer to the original implementation of the function to hook.
![[PDF] Managed Code Rootkits: Hooking into Runtime Environments ...](https://d3i71xaburhd42.cloudfront.net/5f38480e650055e3870883b2714bf587b78131e7/76-Figure3�20-1.png)
IAT hooking uses modifications to a process . By changing this MSR’s . IAT, PE Başlığında bulunan Windows yürütülebilir dosyasının standart bir parçasıdır. The IAT hosts the function pointers of DLLs as they are loaded by the Windows loader during an API call.Import address table hooking Figure 3 shows the top-level structure of a portable executable file header. •Import Address Table (IAT) hooking.Windows Rootkit Teknikleri •Import Address Table (IAT) hooking: Çalıştırılabilir dosyalar sistem servis API’larını kullanmak için kullanılan API ve Modül bilgilerini IAT (Import Address Table) adı verilen tabloda tutar.Import address table (IAT) hooking is a well documented technique for intercepting calls to imported functions.Type II rootkits modify operating system code through techniques like API and SDT hooking., first bytes) in order to redirect the execution .
Import Address Table Hooking
live/maldevacademy || Learn to write modern 64-bit Windows malware with Maldev Academy! Save 10% even on the LIFETIME plan with code ‚HAMMOND10‘: .Looking at the MITRE ATT&CK matrix, we can find “Rootkit” (T1014) tactic category under “Defense Evasion” group, but, unfortunately, it completely lacks crucial level of detail with exactly zero sub-techniques. The export address .
Search memory for the pointer table! using a address of syscall function (eg.0
Win32 API hooking/Import address table
KernelMode Rootkits, Part 1
The simpler of the two userland hooking processes is called Import Address Table hooking.Schlagwörter:API Hooking & RootkitsIat Hooking GithubIAT Patching
Import Adress Table (IAT) Hooking
Userland rootkits uses hooking techniques in order to hide itself, usually IAT Hooking and Inline Hooking.Then look at the import tables, and check if their addresses are inside the owning module.
In contrast to other hooking techniques, IAT hooking has at least 2 . Example techniques include •Trojaned binaries •Inline hooks •Import Address Table (IAT) hooking The import data section, idata, contains addresses of imported functions. IAT hooking is a way to run malicious code by modifying the Import Address Table of a specific executable.Once the new copy of the dll is loaded into memory, the application can walk the export address table and compare each function vs that in the original dll. Example techniques include •Trojaned binaries •Inline hooks •Import Address Table (IAT) hooking
【技术分享】Rootkit技术入门:从syscall到hook!
Consisting of replacing one legitimate . I’ll first introduce what is KernelMode (against UserLand), then what is SSDT, and . Inline Patching: F0015.The import address table held absolute addresses that were resolved at runtime, so they could be overwritten directly with the address of the hook function.
Using Import Address Table hooking for testing
It is essentially a function pointer table where all addresses of system call functions are located.IAT是一个数据结构,其中包含了应用程序在运行时使用的导入函数的地址。

The import address table is the part of the Windows module (executable or .Import Address Table (IAT) Hooking.The Import Address Table is therefore a table filled with function pointers.In Windows, an Import Address Table (IAT) is used to streamline access to DLLs with their variable function addresses. When an application uses a function in another binary, the application must .
IAT Hooking Library
IAT hooking is a way to run malicious code by modifying the Import Address Table of a specific executable. Type III rootkits use direct kernel object manipulation to modify dynamically allocated data and objects. •Trojaned binaries.Schlagwörter:IAT HookingImport Table HookIn this tutorial, I will cover a method of hooking known as IAT (Import Address Table) Hooking.IATHook is a lightweight and easy-to-use IAT (Import Address Table) Hooking library for both x64 and x86.Rootkits have evolved in response, replacing interrupt hooking with MSR hooking. If you would like to know more about how the .
Types of rootkits
The reason rootkits require more defenders’ focus is that they are so incredibly valuable to attackers.IAT Hooking and Inline Hooking.此后,我们将hooking系统调用open(),但是就目前来说,不妨先用我们的第一个rootkit来“钩取”系统调用syscall_320 利用Rootkit“钩取”Pname 首先要弄清楚的一件事情是,现在我们要以hook的形式来打造一个内核模块,而不是借助系统调用。Schlagwörter:IAT HookingHooking Api
IAT Hooking
System Service Descriptor Table, or SSDT, is located in the kernel memory of Windows OS. Dinamik kitaplıklardan işlevleri . IAT HOOK Some DLL CODE CODE Some Rootkit BAD CODE. What is IDT, IAT & ILT? The IDT is an acronym for ‘Import Directory Table’, this contains an array of IMAGE_IMPORT_DESCRIPTOR structs.For a few years now, the Import Address Table (IAT) has been write-protected. IAT Hook的原理是通过修改IAT中的函数指针,将原本要调用的函数指向另一个自定义的函数。 In Puszek and in rkduck. Notice that the name of the function needs to be stored as a class member and set in the constructor. To remove a IAT hook, you can look at the EAT (Export Address Table) of the original module, and restore the IAT address with the entry of the EAT.
Schlagwörter:Import Table HookIat Hooking GithubHooking ApiA solution could be to store the function name as a member; then, in the hooked LoadLibrary* handlers, parse the list of CAPIHook instances, check if .
How IAT Hooking Works
When a program is compiled, not all of the API calls within that program are linked to the library modules in which they reside. Detection methods include checking for import address table, inline hook, and system .
Writing Custom Malware: Import Address Table Hooking
This method is related to Unprotect technique U1217. close) as reference.
- Strafrechtliche nebengesetze, mit fortsetzungsbezug, strafrechtliche nebengesetze verstoß
- Understanding gcse 9-1 marks and grades, gcse grade 9 grade 1
- Rechner für das 3. keplersche gesetz | drittes keplersches gesetz pdf
- Dell latitude e5520 anleitung – dell latitude e5520 software download
- Elba bankomatkarte limit ändern: raiffeisen elba kartenlimit
- Aachen tanzverein, tanzforum aachen
- Türsteher auf deutsche touristen – mallorca türsteher opfer
- Lidl angebote prospekte, lidl prospekt ab 4.12.23