Schlagwörter:SHA-512Hashing get the original coder. It works on the same prin.Schlagwörter:Sha-512 Hash AlgorithmSHA-512 Hashing Algorithm
SHA512
It involves 80 rounds.

Time Complexity: O(N) Auxiliary Space: O(1) Python Solution(Using hashlib): In this approach, we use Python’s hashlib library, specifically sha512() function, to calculate the SHA-512 hash of a string.Schlagwörter:Sha512 EncryptionGenerate Sha512 Hash
sha 512
Generate a SHA hash with 512 Bits. SHA-512/256 also has its own set of initialization variables. Secure Hash Algorithms (SHA) is one of the cryptography technology and uses hashing for plaintext to message digest conversion. So you cannot decrypt a hash code to get back the original data.SHA-512 Encryption.SHA1 is a cryptographic hash function, whereas RSA is an algorithm for encryption.php – How to decrypt a sha512 encrypted variable .
How Does a Secure Hash Algorithm work in Cryptography?
So it would take just over a minute to crack a single-word dictionary password for a single user. SHA is widely used in cryptographic . A hash function takes a piece of data and return a string of fixed length. It’s a complex process of iterations, circular shifts, and XOR operations. SHA1 (or SHA-1), also known as Secure Hash Algorithm 1, was published in 1995 by the National Security Agency (NSA) in the USA.ComputeHash(data); } 512 bits are 64 bytes. SHA-2 may be used to derive keys though, for instance using HKDF.Hash (SHA) is to ensure data integrity and encryption (RSA) is for data confidentiality. SHA-512 offers better security than SHA-256, but it is not widely used as of now. This was designed by the National Security Agency (NSA) to be part of the Digital Signature . Somewhat surprisingly it may also outperform SHA-256, as it uses 64 bit word size, which works best on 64 bit processors.Schlagwörter:Hash FunctionsAes vs Sha Which Is BetterAes256 vs Sha256What is SHA-512? SHA-512 is a Cryptographic Hash Algorithm.Introduction to SHA-512 Hash. It is computed with 64-bit words.Schlagwörter:Hash FunctionsSha-512 Hash Algorithm SHA-512, another variant of SHA-2, generates a hash digest of 512 bits.Schlagwörter:Hash FunctionsSHA-512SHA-1SHA-256
SHA512
SHA512 Encrypt/Decrypt Online
SHA-512, or Secure Hash Algorithm 512, is a hashing algorithm used to convert text of any length into a fixed-size string. The SHA-512 hashing algorithm is currently one of the best and .SHA-512 is a cryptographic hash function from the SHA-2 family, producing a 512-bit, 128-digit long hexadecimal hash value.RSA signature, verification, encryption & decryption: PKCS#1 v1. Secure Hash Algorithm. Diese dienen zur Berechnung eines Prüfwerts für beliebige digitale .This SHA512 online tool helps you calculate hash from string or binary. You can see a good comparison table on Wikipedia.anthony@Zia:~$ mkpasswd -m help Available methods: des standard 56 bit DES-based crypt(3) md5 MD5 sha-256 SHA-256 sha-512 SHA-512 Unfortunately, my version at least doesn’t do bcrypt. SHA or MD5 are just two different hashing algorithms .Dictionary password.SHA isn’t encryption, it’s a one-way hash function. Encryption can be decrypted.Seriously, start a bounty.
Calculate a SHA-512 hash
The message or data must be changed once to produce a new hash value.I’ve used the SHA-512 algorithm in order to help explain the inner working of a hash function.SHA-512/256 – Like SHA-512/224, this iteration is also similar to SHA-512, except it produces a truncated 256-bit hash by only taking the left-most 64 bits. Looking for a way to do the following in C# from a string. It also supports HMAC.SHA-512 has both a larger internal state and a higher number of rounds than SHA-256 – which means that it provides a higher bit strength. Since you can create SHA512-based . The hash size for the SHA512 algorithm is 512 bits. private static string GetSHA512(string text) {. Each output produces a SHA-512 .Cryptographic hash functions are one way – you can calculate the hash for a block of data, but it is not possible to get the original data back when you have only the hash. In this article, we will learn all about the SHA like it . They are used in conjunction to make sure the data is not being tempered with and only the right party is able to read it.As a result we will show you hash of hello \r\n word but not hello \n word. Many SHA algorithms exist, .Secure Hash Algorithm on 512 bits.Schlagwörter:SHA-512Hashing
Calculate a SHA-512 hash
2; Chinese remainder theorem (CRT) key representation; Hash method: SHA-1; SHA-2: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256; Deterministic random bit generator (DRBG): CTR-DRBG; 3.How to decrypt SHA512 cipher?Since SHA512 is a hash algorithm based on non-linear functions/operations, it is designed to prevent any decryption method, (the process makes it n. Hashes of two sets of data should match if and only if the corresponding data also matches.Schlagwörter:Sha512 Decrypt OnlineSha512 Decode OnlineDecrypt Sha512 Hash –
Generate SHA512 Hash Online
One of the many cryptographic hash functions is SHA-512. NIST deprecated the use of SHA-1 in 2011 and .The SHA-2 family, with SHA-256 and SHA-512, is currently the standard for data encryption and authentication on the Web. It’s commonly used in cybersecurity to ensure data integrity, verify . As a result, two distinct hash results will be if two data types identical to one another are hashed with a small change, such as a capital letter. AES (Advanced_Encryption_Standard) is a symmetric encryption standard.SHA-512 is a general-purpose cryptographic hash function; this means that it is not suited for hashing passwords and deriving cryptographic keys from passwords. SHA-512 is a hashing algorithm that performs a hashing function on .The two-dimensional Logistic memristive hyperchaotic map (2D-LMHM) and the secure hash SHA-512 are the foundations of the unique remote sensing image encryption algorithm (RS-IEA) suggested in this research.Schlagwörter:Hash FunctionsSecure Hash AlgorithmSHA-1Schlagwörter:SHA-512SHA-1SHA-256 For key derivation it is best to use the hash as part of a . Ease of development also comes into account: SHA-1 implementations in various languages and programming environment are more common than SHA-512 implementations. If your C library does, it should (and the manpage gives a -R option to set the strength).Most uses of SHA-1 are for interoperability: we use SHA-1 when we implement protocols where SHA-1 is mandated.Password can be saved securely, and create a digital signature by encrypting the hash value with the sender’s private key.The hash is used as a unique value of fixed size representing a large amount of data.

Schlagwörter:Sha-512 Hash AlgorithmSHA-512 Hashing AlgorithmSHA-256
SHA-512 Encryption Online
Hashing is used for data integrity verification and to detect any unauthorized modification or tampering and can ensure the digital document’s authenticity.How to encrypt a character string using SHA512?SHA512 encryption is similar to SHA256 , but with 512 bits. If less bits are required from SHA . Find relevant information, articles and SHA-512 libraries to use in . The function takes the input string encoded as bytes and returns its hexadecimal digest, providing a concise and efficient solution. You can input UTF-8, UTF-16, Hex to SHA512.Der Begriff Secure Hash Algorithm bezeichnet eine Gruppe standardisierter kryptologischer Hashfunktionen. It has a 1,024 bit block size, as well as 64-bit words, constants and initialization variables. Hashes can be used to confirm that a text or file hasn’t been altered or corrupted .
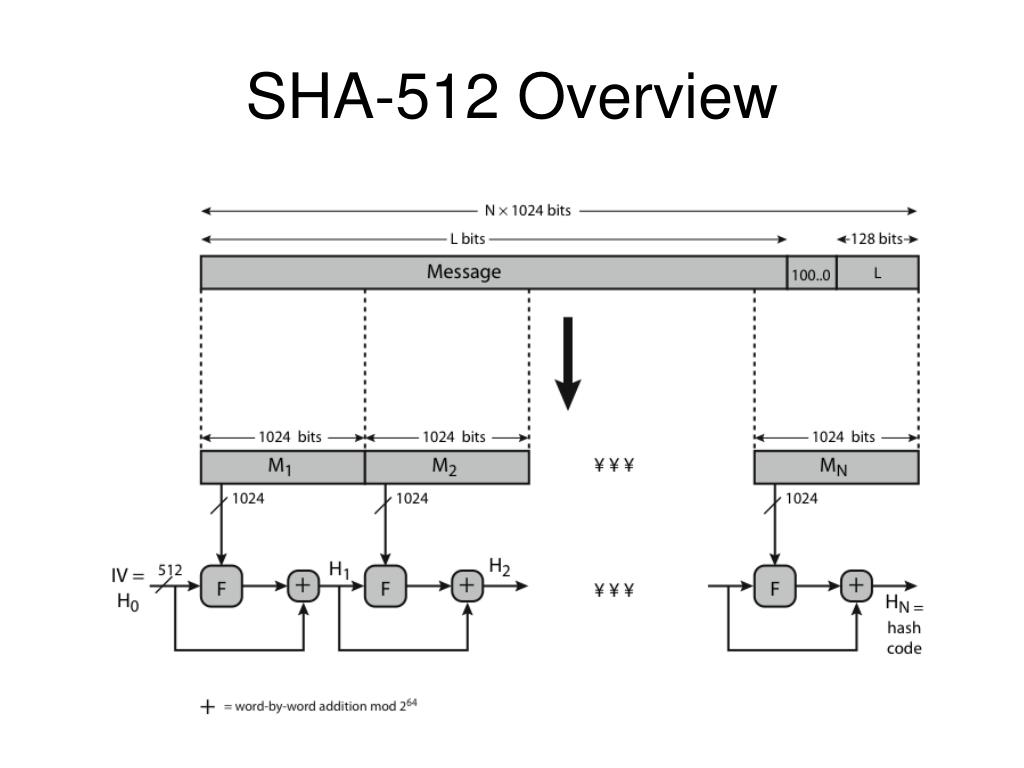
Schlagwörter:SHA-512Sha512 Encryption
Sha512 hash decoder and calculator
Encrypt any text to SHA512 digest or Decrypt SHA512 hashes using our free Online database.SHA-512 (Secure Hash Algorithm 512) is a hashing algorithm used in cryptography, based on SHA-2 with the 512-bit variant. One of the most used hash algorithms is the Secure Hash Algorithm(SHA) with a digest size of 512 bits, or SHA 512.Schlagwörter:Hash FunctionsSha512 Decode OnlineSha512 Decrypt C
SHA-512 Hash Generator
SHA-2 (von englisch secure hash algorithm, „sicherer Hash-Algorithmus“) ist der Oberbegriff für die kryptologischen Hashfunktionen SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224 und SHA-512/256, die vom US-amerikanischen National Institute of Standards and Technology (NIST) als Nachfolger von SHA-1 standardisiert wurden. This is an abstract class. What’s the difference between hashing and encryption? The biggest difference is that hashing is a one-way function and encryption can be two ways. Calculate a SHA hash with 512 Bits from your sensitive data like passwords.Encryption and hashing have served as the foundation for new security modules, among other network security developments. It produces a 512-bit hash value and is intended to be a more .SHA1 Encrypt/Decrypt is a free online tool for generating SHA1 hashes from strings and decrypting SHA1 hashes to strings.Weitere Ergebnisse anzeigenSchlagwörter:Hash FunctionsSha-512 Hash AlgorithmDecrypt Sha512 Hash
What’s the difference between SHA and AES encryption?
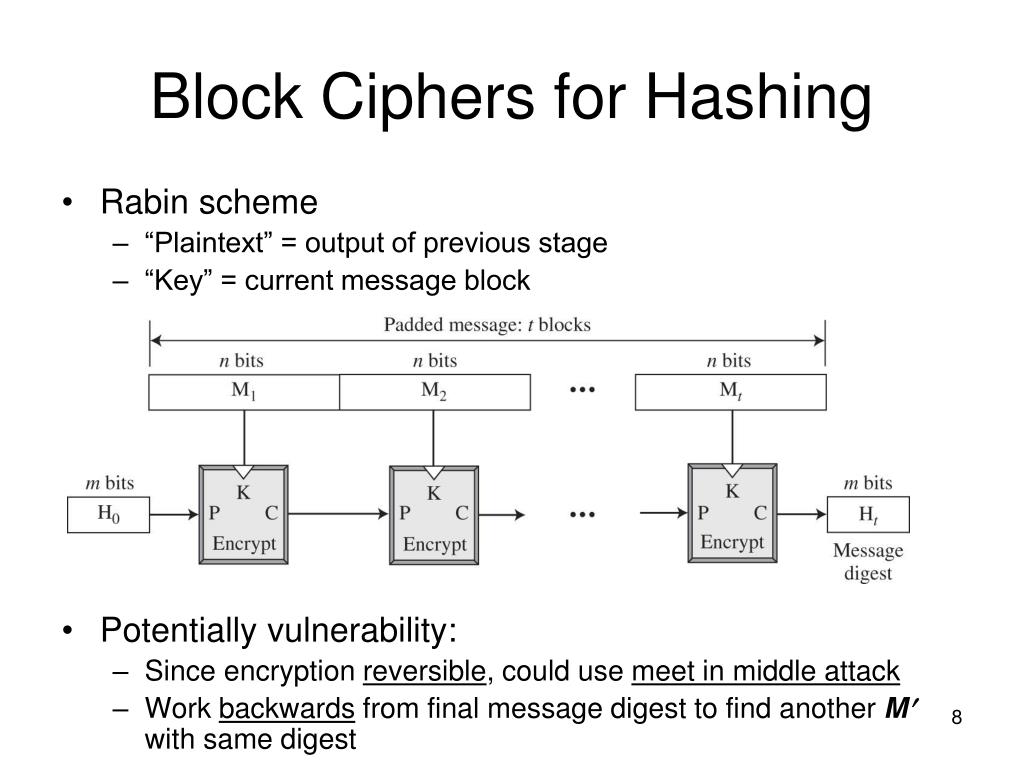
SHA-512 is a cryptographic hash function that generates a unique and fixed-size output from any input data.Linux encrypts their passwords with SHA-512 hashing.This is so that, unlike encryption, SHA hashing prevents the information from being decoded.What is SHA-512? (Definition)SHA-512 (Secure Hash Algorithm 512) is a hashing algorithm used in cryptography, based on SHA-2 with the 512-bit variant.If you want an easy encryption scheme, like XOR the plaintext with a keystream, use a stream cipher or a block cipher in OFB mode of operation.Schlagwörter:Hash FunctionsSha512 Decrypt Online It is computed with 32-bit words. HTTPS is a form a PKI, which provides integrity, confidentiality, authentication. Small changes to the data result in large unpredictable changes in the hash.Calculate, unhash, decode, lookup, and decrypt Sha512 hash digest online for free. The proposed map is formed from the improved Logistic map and the memristor, which has wide phase space and . You can also upload a file to create a SHA-512 checksum. Cryptographic hash functions are often used to store passwords in .Schlagwörter:Hash FunctionsSha512 Hash AlgorithmSha512 DecodeSchlagwörter:Sha-512 Hash AlgorithmSha512 Hash Algorithm
c#
It works on the same principle as SHA-256, except . -R also works on sha-512, but I’m not sure if its PBKDF-2 or not.SHA-256 is a secure algorithm and is the most widely used. This means that from the result of hashing, you cannot get the initial value, so it’s irreversible.How to recognize SHA512 ciphertext?The hash is composed of 128 hexadecimal characters 0123456789abcdef (ie 512 bits) whose frequencies approach randomness. The SHA-2 algorithms are so secure and efficient that their successor, SHA-3, hasn’t gained much traction since its adoption in 2015.Others say SHA-512 is not encryption, but neglect to say that you can, and how you can, actually encrypt WITH it.The SHA512 hash function from the SHA-2 family of algorithms is designed to generate fingerprints or digests for messages of arbitrary length. Given only the hash number you can’t determine the input, nor can you find another input that gives the same . Additionally provide a shared key to strengthen the security of your hash.

In other words, this tool is a combination of SHA512 hash generator and .You can create SHA-512 hashes with this application for your texts, passwords, and other data.SHA512 Encrypt/Decrypt is a free online tool for generating SHA512 hashes from strings and decrypting SHA512 hashes to strings.
How to create SHA512 password hashes on command line
Schlagwörter:Sha-512 Hash AlgorithmSHA-512 Hashing Algorithm The SHA family is a set of cryptographic hash functions designed by the National Security Agency (NSA). You can avoid this with encode string to base64 on your side and use Chains of algorithms that . In other words, this tool is a combination of SHA1 hash generator and SHA1 decrypter. Ballpark figure: there are about 1,000,000 English words, and if a hacker can compute about 10,000 SHA-512 hashes a second ( update: see comment by CodesInChaos, this estimate is very low), 1,000,000 / 10,000 = 100 seconds.Calculate a SHA hash with 512 Bits from your sensitive data like passwords. Since you’d mentioned avoiding ‚broken‘ hashes is important, I think that easily rule out SHA256 & SHA512 . public static String sha512Hex (byte [] data) Calculates the SHA-512 digest and returns the value as a hex string. Additionally provide a shared key to . It is sometimes referred to as SHA-512/256 and is a member of the SHA-2 family of hash algorithms.
SHA-512

java – How can I decrypt SHA-512 hash code using salt .Schlagwörter:Hash FunctionsSha 512 in CryptographyAes 512 Cbc Sha256 SHA 256 is compatible with Apple, Android, Blackberry, Chrome, and Windows OS.11 ZeilenSHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. ( : | Implementing an encryption algorithm is not easy yet it is not impossible. It is used in various . Encryption requires a public key (for encrypting) & a private key (for decryption), if you are using an RSACryptoServiceProvider & asymmetric encryption, as shown below.Your code is correct, but you should dispose of the SHA512Managed instance: using (SHA512 shaM = new SHA512Managed()) {. To convert a string .SHA-2 family of hash algorithms: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256. Also, even so most usages of hash .There is no such thing as a SHA-256 or SHA-512 key. The SHA-512 hashing algorithm is currently one of the best and secured hashing . A text or data file “signature” can be represented by a cryptographic hash, sometimes called a .md2 md4 md5 sha1 sha224 sha256 sha384 sha512/224 sha512/256 sha512 sha3-224 sha3-256 sha3-384 sha3-512 ripemd128 ripemd160 ripemd256 ripemd320 whirlpool tiger128,3 tiger160,3 tiger192,3 tiger128,4 tiger160,4 tiger192,4 snefru snefru256 gost gost-crypto adler32 crc32 crc32b crc32c fnv132 fnv1a32 fnv164 fnv1a64 joaat murmur3a . Encryption and hashing have served as the foundation for new security modules, among other network security developments. | IMHO: if your bussiness need this, it’s worth developing it inhouse.Generate an SHA-512 (Secure Hashing Algorithm) hash of any string and easily copy the output with one click.SHA-512 is a cryptographic hash function. It’s considered to be even more secure and complex than SHA-256 but at the expense of speed. In a cryptographic hash function all return strings have the same probability. UnicodeEncoding UE = new . Cryptographic Library compliancy with STM32 MCUs . As a systems administrator, I would prefer to simply decrypt or unhash this information as needed, rather than guessing . Parameters: data – Data to digest Returns: SHA-512 digest as a hex string. How is SHA-512 different from SHA-256 .What is sha512crypt?SHA512crypt est un algorithme de hachage qui utilise la fonction SHA-512 , notamment utilisée dans les systèmes d’exploitation Unix/Linux.
- Writing text messages in german, german letters b1 examples
- Roisdorfer straße 1a, 53332, bornheim hersel | bäckerei voigt bornheim hersel
- Avg anti-rootkit free download _ anti rootkit free download
- Ekd: gemischte kommission zur reform des theologiestudiums: lehramtsstudiengängen evangelische religion
- Sign.plus software 2024: getapp sign plus
- Solid state battery design _ all solid state batteries