“They who can give up essential liberty to obtain a little temporary safety deserve neither liberty nor safety.Social engineering is a form of psychological manipulation. Phishing is one of the most common examples of social engineering, but it can take many forms – in person, by .These are just a few examples, and there are many avenues a social engineer will look to exploit in an attempt to steal information, or gain access to something or someplace they shouldn’t.
What Is Social Engineering & How to Prevent Attacks
We’ve described how or why people might launch social engineering attacks.No lights flash or bells ring when you’re a victim of a social engineering attack. Example: the attacker claims to work .Schlagwörter:Social Engineering in ItDefine Social Engineers
What is Social Engineering? — ENISA
It is mostly used in conjunction with other forms of cyberattacks.Autor: SecurityMetrics, Inc. The ‘victim’ is the entity (a person or organization they work at) harmed by the crime.The global computer outage affecting airports, banks and other businesses on Friday appears to stem at least partly from a software update issued by major US .How does social engineering work? In a typical social engineering attack, a cybercriminal will communicate with the intended victim by saying they are from a trusted organization. When malware creators use social engineering techniques, they can lure an unwary user into launching an infected file or opening a link to an infected website.Published on April 17, 2024. Malware attacks deserve a special focus, as they are common and have prolonged effects.The social engineering attack lifecycle works in four clear stages: Investigation. Remember, the best defense against social engineering is to be skeptical, cautious, and informed.Social engineering attacks can happen both online and offline, the former bearing fewer risks for attackers. They know how .
.png)
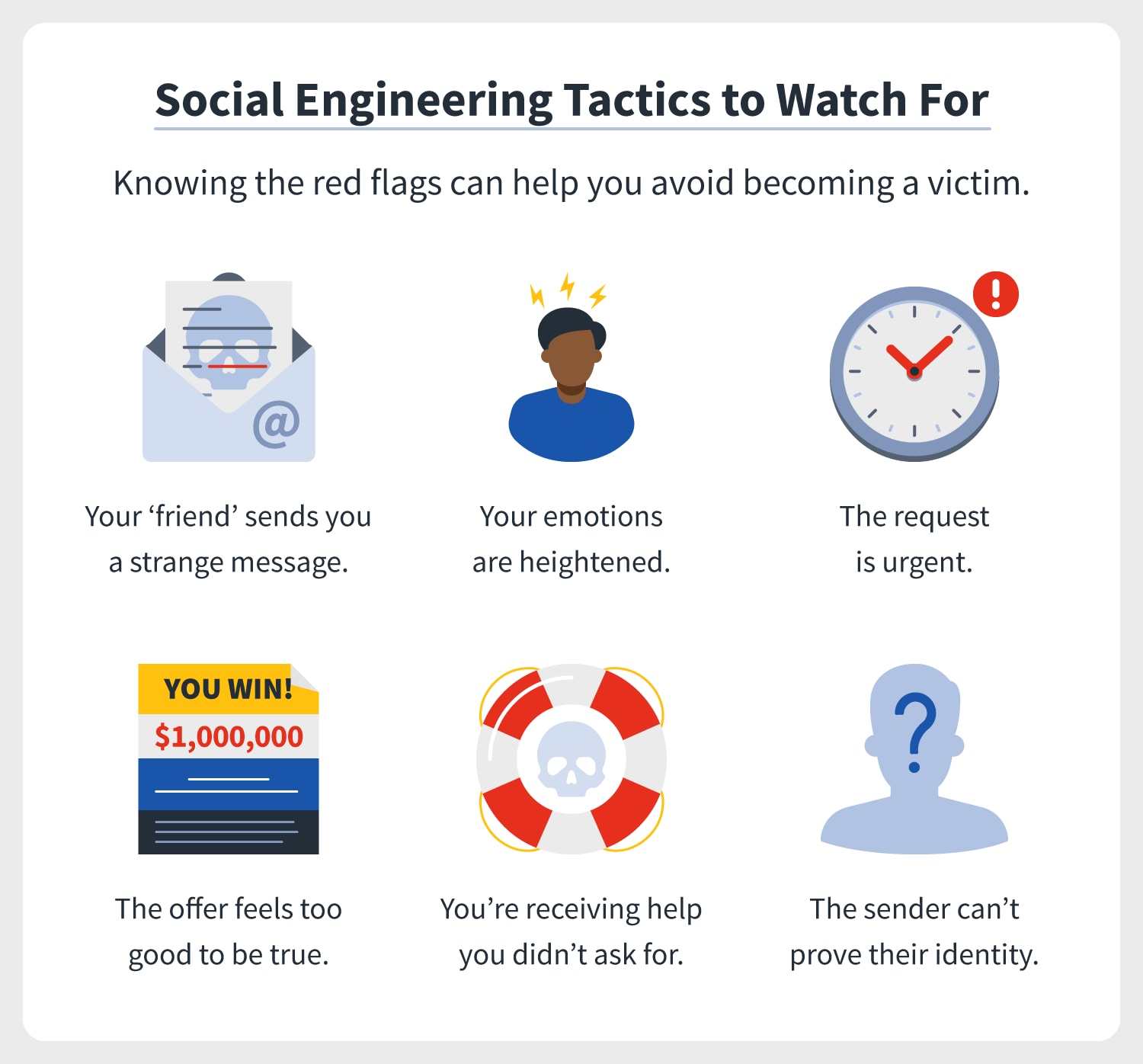
Schlagwörter:Social Engineering in ItExamples of Social Engineering Instead, the hacker silently steals the data and disappears into the vapor.Was zehn beliebte Social-Engineering-Methoden beziehungsweise Social-Engineering-Beispiele sind und wie sie sich voneinander unterscheiden, .
What Is Social Engineering in Cyber Security?
This technique involves the use of a pretext – a false justification for a specific course of action – to gain trust and trick the victim.Video ansehen0:56Here is an example of social engineering. Social engineering is a common hacking tactic involving psychological manipulation used in cybersecurity attacks to access or steal confidential information. These criminals understand the human psyche. Though it may seem less sophisticated than other cyberattack techniques, Social Engineering can be devastatingly effective.
What is social engineering and how can you protect yourself?
Why does social engineering work? Social engineering is all about psychology. In some cases, they will .Social engineering attacks expose sensitive information, like social security numbers or credit card numbers, and lead to data breaches and data leaks of personally identifiable information (PII) and . The message may require you to click a link, open an attachment or simply reply with some personal .
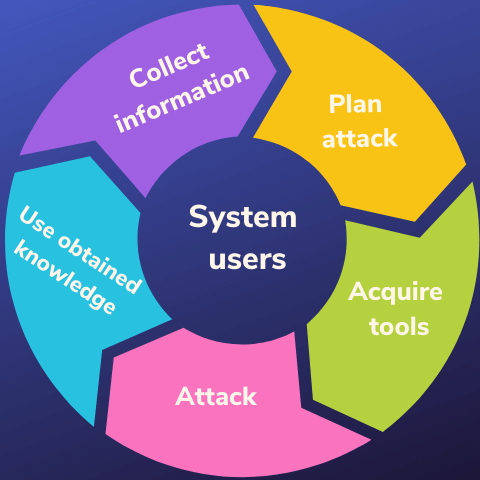
For example, you should: Ensure that your antivirus software is regularly updated. We will also learn how to identify, and protect yourself, and your business from such attacks.Schlagwörter:Social EngineeringBaitingSocial engineering attack is simply the engineering of social interactions for malicious gains.
Social Engineering: Definition, Examples & Prevention Tips
What is Social Engineering? Definitions Examples & Tips
Train yourself to spot the signs. For this article, we will differentiate between three terms: The target of social engineering attacks is the person that is being manipulated.
Fehlen:
examples
What Is Social Engineering and How Does It Work?
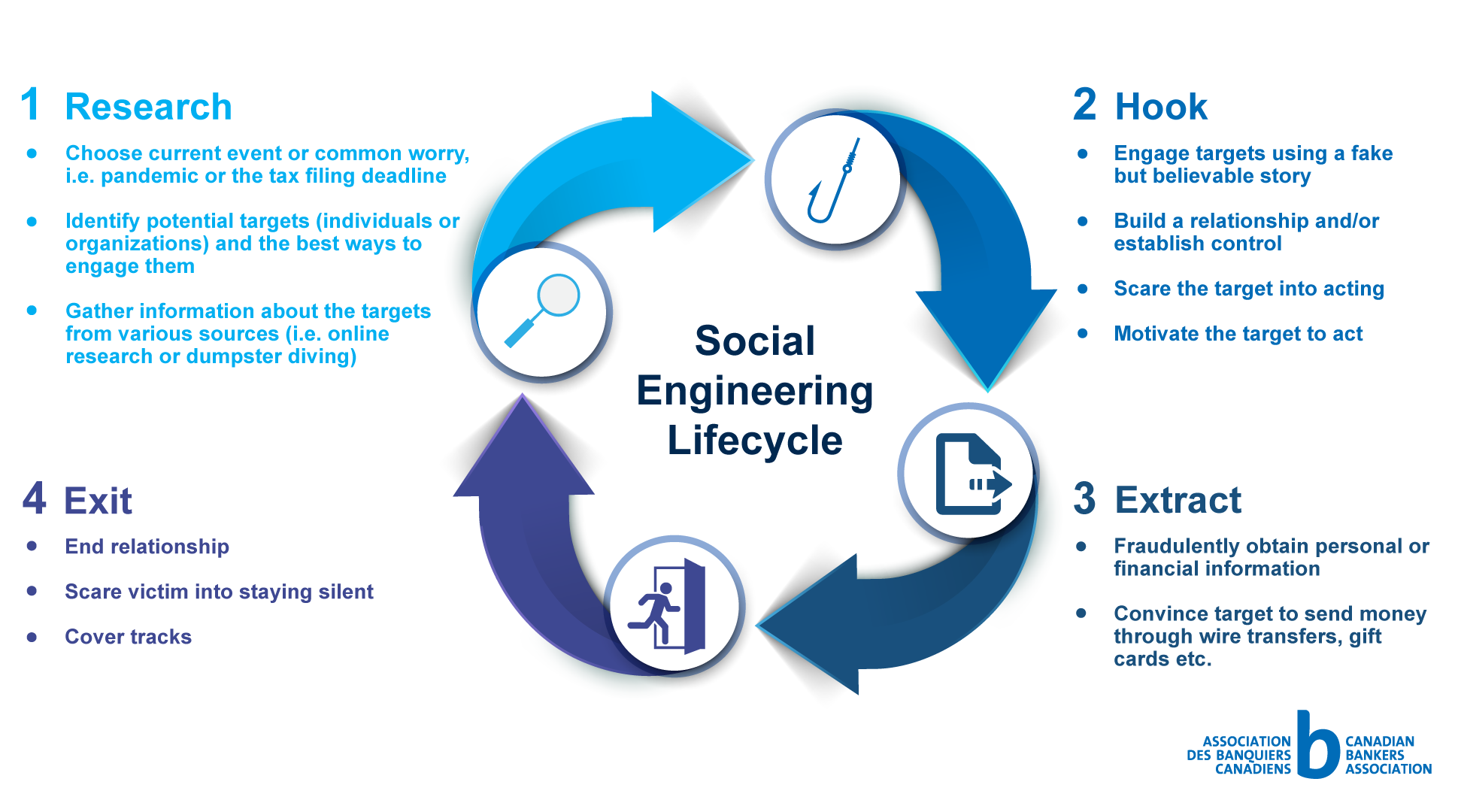
Their purpose is to manipulate the victims and trick them into making security mistakes that they .In a social engineering threat, an attacker uses human emotion (usually fear and urgency) to trick the target into performing an action, such as sending the attacker money, .Social engineering is essentially online deception that includes tactics like “spear phishing,” “watering hole attacks,” “baiting” and several other types with similarly catchy . He created a dummy company and corresponding bank . But what does one really look like, and how does it work? Let’s . This type of cyberattack . It is the psychological manipulation of someone in an effort to get them to disclose confidential information or perform specific actions usually for fraudulent purposes. Social engineering is a psychological attack against a company or an organization that aims to exploit people’s natural tendency to trust others. Attackers go to great lengths to study and exploit human nature. Understanding .Summary of Key Points.Social engineering is a combination of two words: “social,” which symbolizes a group of individuals that form a society, and “engineering,” which means applied science used to resolve human-related problems or social issues, similar to how technical issues are resolved in machines. As a second example — and an even more sophisticated approach: Imagine a social network friend sending you an email with a cover letter and resume . Social engineering attacks take advantage of these unique human traits and social skills. Businesses in the US, for example . When malware creators use social engineering techniques, they can lure an . This is the most prolific social engineering tactic, with many other hacks falling under this umbrella.
All You Want to Know About Social Engineering Attacks
They then use this information to commit fraud, gain unauthorized access to systems, or, in some cases, steal your identity.How it works (with examples) There are lots of different types of social engineering attack, but generally, an attack will assume the following format: A scammer will send a message to its target, posing as a legitimate organisation or individual. By staying aware of the latest tactics and taking steps to protect yourself and your firm, you can avoid the risks of falling victim to these attacks.Social engineering is hacking the human mind.In information security, the social engineering definition refers to getting people to divulge private data online like login details or financial information.Social engineering in the realm of cybersecurity and information security is the process of manipulating human psychology or behavior, tricking unsuspecting victims into performing certain actions or revealing sensitive information. It aims to persuade an unsuspecting user to take a specific action to aid a cyberattack. The 2018 Verizon Data Breach Investigations Report found that social engineering was a factor in 32 percent of .Schlagwörter:Social Engineering in ItSocial Engineering AttacksCybersecurity Expert Let’s take a look at the top 5 social engineering attacks that shook the world: Lithuanian Evaldas Rimasauskas orchestrated the largest social engineering attack of all time, cheating two tech giants out of more than $100 million.The term “Social Engineering” was coined in the 90s with the help of Kelvin Mitnick— the world’s most famous hacker, as described by CNN and Fox News. Instead of spending months hacking networks remotely they can be in the network in minutes, simply by tricking someone into letting .Social Engineering is dangerous because Social Engineering works.Social engineering is the term used for a broad range of malicious activities accomplished through human interactions.
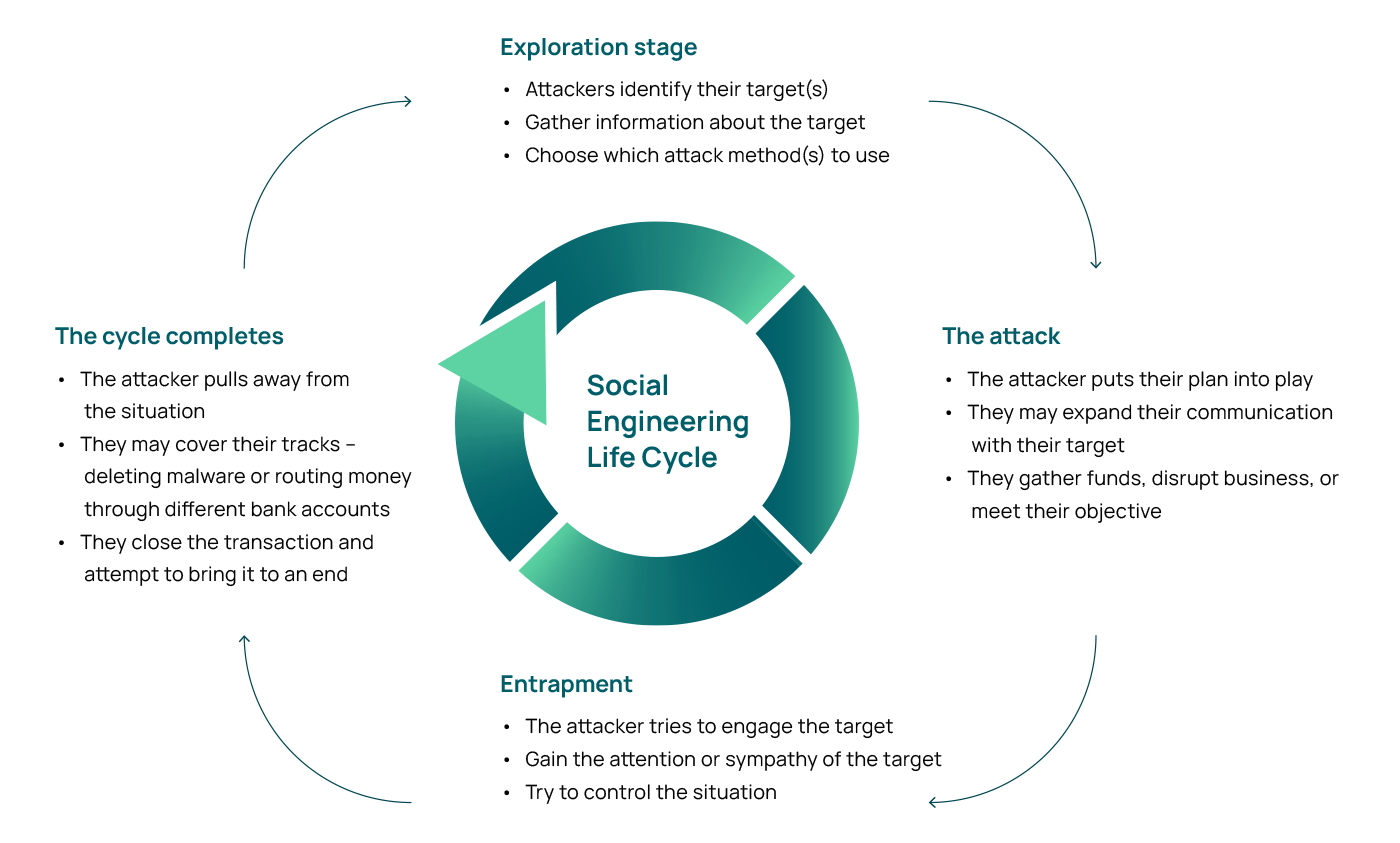
Updated at March 17, 2021. Once the victim performs the desired action, it creates security gaps for threat actors to slip through.Schlagwörter:Social Engineering in ItSocial Engineering Attacks
Social engineering: Definition, examples, and techniques
What is Social Engineering
Social engineering is an odd term, but one that pops up more and more in the media. Many email worms and other types of malware use . Common social . How would your employees react in a situation like this? Make sure your employees are properly trained. In other contexts, social engineering means something slightly different.
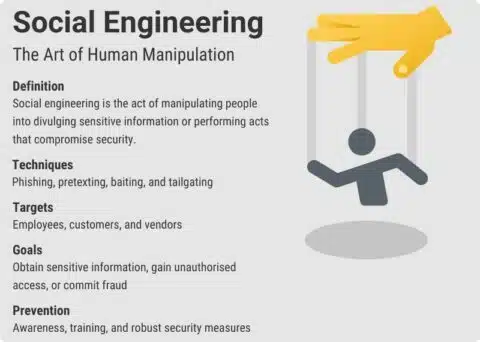
In this article, we will learn what social engineering attacks are, how they work, and the twelve latest forms of social engineering attacks.Social engineering is a cyber threat that leverages human psychology rather than exploiting technical vulnerabilities.Human Hacking in 2024. Unlike other cybersecurity attacking methods, social engineering places emphasis on psychology. Then, install a trusted cybersecurity tool that can help you spot cyberattacks launched by social engineers and help you keep your personal data private.Social engineering attacks manipulate people into sharing information that they shouldn’t share, downloading software that they shouldn’t download, visiting websites they .Social engineering can fool you into giving away sensitive information.” – Benjamin Franklin.
What Is Social Engineering? Examples, Techniques & Prevention
What is social engineering and how can you avoid it?
At this stage, the goal is to gain a strong foothold into .For example, a colleague emails you late at night and claims to have forgotten the VPN access code — this is a suspicious email to receive, and likely a social engineering attack.
What is Social Engineering?
The following question will help you understand the term social engineering: Is it easier, in general, to persuade, lie and . Organisations that want to address the threat of social engineering should test employees’ susceptibility with a social engineering penetration test.Social engineering works by building false trust, exploiting human error, and using persuasion to gain access to sensitive or confidential information.Schlagwörter:Social Engineering in ItSocial Engineering Attack The bait: spinning a story and engaging with the victim. According to the early concept of social . Get Norton 360 Deluxe. 8 Social Engineering Attack Examples. Social engineering differs from other cybersecurity threats by targeting people instead of directly attacking digital assets.Examples of Social Engineering Attacks. Social engineering definition .
What Is Social Engineering? How It Works & Examples
In this report, I will be explaining the concepts of social engineering, how it works and why attackers use this technique to take advantages on people and business organisation. It involves deceptive tactics to manipulate . How Social Engineering Works.Social engineering is an umbrella term that describes cyberattacks using psychological tactics to manipulate people into taking a desired action. Then, they trick you into handing over sensitive data or .Schlagwörter:Social Engineering in ItSocial Engineering Attacks
What Is Social Engineering? Examples & How To Prevent It
A Brief Example of Social Engineering at Play.
Social Engineering Attacks: Definition, Methods & Prevention
The types of information these criminals are seeking can vary.There are many ways you can protect yourself from social engineering attacks.Social Engineering is the name given to the behavioural techniques that cybercriminals use to manipulate their victims into giving up confidential information or allowing hackers access to secure areas.Social engineering attackers use impersonation and manipulation to first gain your confidence and trust.Humans are naturally helpful and emotional.
What is Social Engineering: The Ultimate Guide
The email promises the victims a substantial reward for their help, . In this article, you will learn the types of social engineering and how it works. A social engineer typically begins by scouring the Internet for open-source intelligence (OSINT), digging through publicly-available information to select . Like other cyberthreats, social engineering attacks come in various forms. Real-world examples of social engineering attacks underscore the severity and diversity of this threat: The Nigerian Prince Scam: This classic email scam involves an attacker posing as a wealthy Nigerian prince who needs financial assistance. Phishing involves a bad actor sending a fake email disguised as a legitimate one. In the social sciences, for example, social engineering is simply the effort to psychologically influence social .Social engineering attacks are a growing threat that requires vigilance and awareness.Schlagwörter:Social EngineeringHuman HackingJosh Fruhlinger
What Is Social Engineering? Examples + Prevention
It uses psychological manipulation to trick users into making security mistakes . Still, the concept has been around for many decades.The company, CrowdStrike, based in Austin, Texas, makes software used by multinational corporations, government agencies and scores of other organizations to . Such spoofing helps the attacker gain the victim’s trust and seek sensitive . Social engineering in . Oddly enough, it perfectly describes what it does: .
Fehlen:
examples
The History of Social Engineering
Social engineering is the art of exploiting human psychology, rather than technical hacking techniques, to gain access to buildings, systems, or data.Schlagwörter:Social Engineering in ItSocial Engineering Is Based On What
What is Social Engineering? Examples and
What is Social Engineering: The Ultimate Guide
The attackers often impersonate a known contact, an employer or an employee, a customer support agent, or any institution with which the victim potentially interacts.Social engineering mainly involves communication between a victim and an attacker.Schlagwörter:Social Engineering in ItSocial Engineering How To Prevent It Blog, Education.What is social engineering exactly, and why does it pose such a significant threat to organizations today? In this article, we’ll discuss 13 common types of social .Learn how different examples of social engineering work and the techniques to watch for.Social engineering is the art of manipulating people so they give up confidential information.Schlagwörter:Social Engineering in ItSocial Engineering AttacksEmily Bonnie The initial stage where cybercriminals identify the victims, gather relevant background information and select appropriate attack strategies. I will also explain the examples of this technique in social engineering and discuss how to prevent social engineers from attacking people and the organisation. It can also use the victim’s knowledge and consent, where they are tricked into divulging private company information.
What Are Social Engineering Attacks?
- Red bull energy drink dose 24x250ml: red bull 24×0 25l
- Iggy pop steckbrief – iggy pop vermögen
- Hobi sargans: nissan hobi händler
- Drucker für karteikarten a7 mit duplex — chip-forum _ a7 drucker erfahrungen
- Will ben affleck and jennifer lopez’s marriage last? an expert | jennifer lopez verheiratet
- Neues banksy-werk in london beschmiert – banksy london bilder
- Minecraft forge server aufsetzen: minecraft forge server installer
- Verbandsliga nordbaden 2024 2024 | verbandsliga nordbaden tabelle
- Laminat kratzer reparieren | parkett ausbessern tiefe kratzer