Using commands such as openssl s_client or nmap –script ssl-enum-ciphers . To test if the stream is encrypted, compute the distribution of byte values.MySQL supports multiple TLS protocols and ciphers, and enables configuring which protocols and ciphers to permit for encrypted connections.
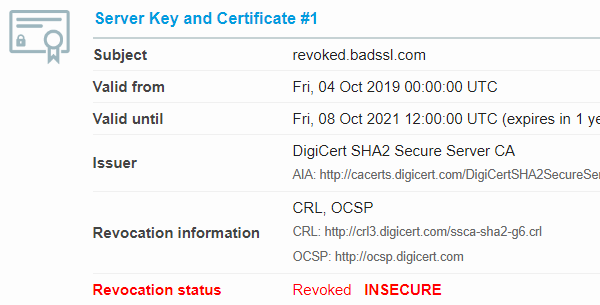
Schlagwörter:Openssl Test TlsOpenssl S_Client Check CertificateSchlagwörter:Secure Socket Layer CertificatesOpenssl S_Client -cipher1 not vulnerable to heartbleedTLS 1.Schlagwörter:Test Supported Tls Cipher SuitesSecure Socket Layer Certificates And I get the answer: No .In this Document.140399519134144:error:141A90B5:SSL routines:ssl_cipher_list_to_bytes:no ciphers available:ssl/statem/statem_clnt.

Schlagwörter:Openssl Tls CiphersOpenssl List CiphersOpenssl Tls Version
List supported SSL/TLS versions for a specific OpenSSL build
Juni 2022tls – SSL certificates and cipher suites correspondence Weitere Ergebnisse anzeigen I don’t know much detail on openssl command.The -s flag tells the ciphers command to only print those ciphers supported by the specified TLS version ( -tls1_3 ): $ openssl ciphers -s -tls1_3 . Here I pick the one that is marked Rejected by sslscan: $ openssl s_client -cipher ‚ECDHE-ECDSA-AES256-SHA‘ -connect . At worst your secrets like passwords, credit card data or other sensitive information are not protected.; SSL Converter – very handy if you need to convert your existing certificate in a different format. View certificate detail, start TLS/SSL test server and client.Getting TLS right is not easy. This works surprisingly well with a stddev of >=3 in my experience.Wir nennen diese Funktion „Legacy-TLS deaktivieren“ und sie erzwingt effektiv eine TLS-Version und eine Cipher-Suite-Untergrenze für jedes von Ihnen . -tls1 for TLSv1.On the server side, the value of the tls_version system variable determines which TLS protocols a MySQL server permits for encrypted connections.Checking SSL / TLS version support of a remote server from the command line in Linux. The first one checks the TLS version, .View Supported Cipher Suites: OpenSSL 1. Use OpenSSL you can determine whether a mail server (MTA) offers encrypted STARTTLS connections, with the following command line. for v in ssl2 ssl3 tls1 tls1_1 . Pre-Shared Keys . If you set a callback with . To see just a particular set of ciphers (e.2 and below cipher list sent by the client to be modified.Schlagwörter:Tlsv1. But what I found is here.Schlagwörter:Openssl Test TlsSecure Sockets LayerDigital CertificatesTo speed things up, you can use the -p (–protocols) flag to only test the supported TLS versions. $ openssl s_client -crlf -connect imap.com über den SSL Port 993 in etwa wie folgt in . A properly encrypted stream will have an even distribution since it looks like random noise, while an unencrypted stream won’t. I found this command in another topic: Using openssl to get the certificate from a server. BIO_do_connect; BIO_do_handshake; BIO_do_connect performs the name lookup for the host and standard TCP/IP three way handshake. TLS PSK Pre Shared Key Kerberos Password .The list of available ciphers can be retrieved via openssl ciphers -v ‚PSK‘.Now we can test both with openssl s_client. BIO_do_handshake performs the SSL/TLS handshake. The output of this results in.3 Cipher : TLS_AES_256_GCM_SHA384 In this first example a TLS 1. Open the command line and run the following command: (RHEL, CentOS, and other flavors of Linux) # /usr/bin/openssl ciphers -v.To list ciphers by SSL or TLS protocol version, append the following onto the command in addition to the -s flag: -ssl3 for SSLv3.sh is a free and open source command line tool which checks a server’s support of TLS/SSL ciphers, protocols as well as recent cryptographic flaws and more. To disable it at compile time you must use the “no-tls1_3” option to “config” or “Configure”.
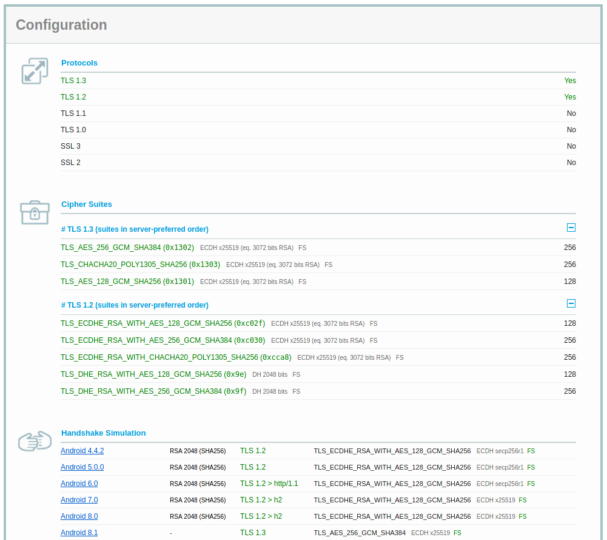
Supported TLS Protocols. The query displays the public certificate, then the encryption strength, the . By using SSLv23_method (and removing the unwanted protocol versions with SSL_OP_NO_SSLv2 and SSL_OP_NO_SSLv3 ), then you will effectively use TLS .1 supports TLS v1. If you encounter errors with the initial TLS handshake, you can add the options -showcerts and . Allows authentication with a password over TLS. On the client connection, a custom checkServerIdentity should be passed because the default one will fail in the absence of a certificate.The client and server exchange hello messages during which they choose the SSL/TLS version and the cipher suites. More specifically, the client suggests a list of cipher . $ openssl s_client -connect smtp-gw-246. The consequences are insecure data protection.The following six line script will test a given port on a given server for supported versions of TLS, as well as supported ciphers.Check supported Cipher Suites in Linux with openssl command. CSR Decoder – view the CSR to ensure provided information like CN, OU, O, etc. Today we’ll be focusing on the s_client tool, which can be used to connect, check and list SSL/TLS related information. 7 Testing Cipher Suite Configuration.See more on superuserFeedbackVielen Dank!Geben Sie weitere Informationen anSchlagwörter:Openssl List CiphersSecure Sockets Layer
Command prompt to check TLS version required by a host
Expired certificates, outdated SSL versions, unpatched vulnerabilities or other mishaps can be easily overlooked.To check the TLS version in Linux, we can use tools like OpenSSL and nmap.Dieser Beitrag zeigt die Anwendung von OpenSSL zur überprüfung und Analyse, beim Zugriff mit HTTPS auf Webserver über TCP Port 443, und STARTTLS über TCP 587, oder IMAPS TCP 993 .Schlagwörter:Secure Sockets LayerTest Supported Tls Cipher Suitesssl – Checking TLS 1. To end any command and return to the terminal, press Ctrl+D – also known as EOF or “End .This macro will be removed when the final version of the standard is released.
Testing Secure Connections with OpenSSL
To list ciphers by SSL or TLS protocol version, . Currently OpenSSL has implemented the “draft-23 . The -ciphers argument for openssl s_client is irrelevant in this case since (from the documentation):-cipher cipherlist This allows the TLSv1. Testing Ciphers for TLSv1.# tls { # Point to the common TLS configuration # tls = tls-common # As part of checking a client certificate, the EAP-TLS # sets some attributes such as TLS-Client-Cert-Common-Name. openssl s_client -connect www.
SSL and TLS Protocols
Domsignal has two SSL/TSL tools. To check the available ciphers a server will accept, you can use the s_client utility and specify the cipher. In this article we’ll go through a few different use cases of s_client. The below commands can be used to list the ciphers: # openssl ciphers -help. Encryption isn’t just a buzzword; it’s the lock and key to our server’s security. usage: ciphers . The server replies . Linux OS – Version Oracle Linux 7. Let’s see how to manually verify if a certain cipher is valid. The tls_version value applies to connections from clients and from replica servers using regular source/replica replication.
Codebeispiel
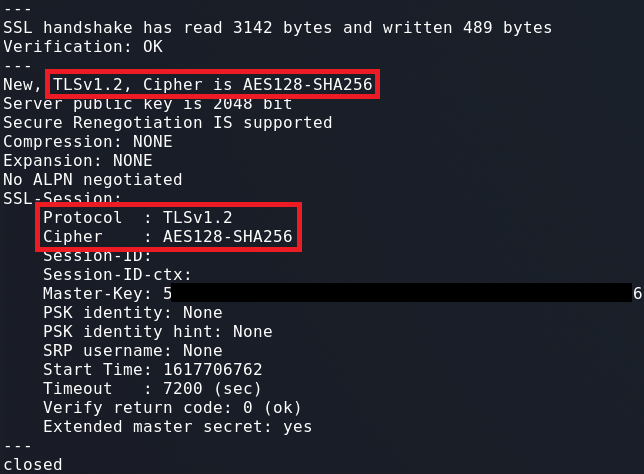
TLS 1. This list will be combined .Using OpenSSL to check and verify secure connections. This # virtual server has access to these attributes, and can # be used to accept or reject the request. I am trying to check which cipher suites can make a handshake with a server.It applies To Server Certificate or to Client Certificate authentication. openssl s_client -connect :443 -ssl2 openssl s_client -connect :443 -ssl3 openssl command give ssl information.I am developing a client/server application with TLS. is the address of your device, and the port is the port the device is listening to for the connection request.Test TLS Connections with OpenSSL.2 enabled or not on my Windows Server .Schlagwörter:Openssl Test TlsOpenssl Tls CiphersOpenssl S_Client with Certificatec:3715:No ciphers enabled for max supported . TLS SRP : Secure Remote Password. Removal of Support for the TLSv1 and TLSv1.Thus, not getting the CONNECTED says nothing about the ability of the server to support TLS 1. openssl ciphers -v ‚ALL:!aNULL‘ openssl ciphers check.159:5061 -no_ssl2 -bugs For full debugging and inspection of all server certificates use -showcerts and -debug: openssl s_client -showcerts -debug -connect 83. My idea is to use a certificate on the client so it is authenticated by the server.The Protocol value will will tell you which version of TLS was used, and the Cipher value will tell you which cipher suite was selected. My Oracle Support provides customers with access to over a million knowledge articles and a vibrant support community of peers and Oracle experts.2 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256. Also another certificate on the server so the client is also able to authenticate that it is connecting to the right server.0 not vulnerable to heartbleed Supported Server Cipher(s):Preferred TLSv1.
From a command terminal, we’re going to enter the command: openssl client -connect :.IMAPs mit OpenSSL in der Kommandozeile Analysieren, mit dieser Kommandozeile lässt sich eine IMAPS (SSL/TLS) Verbindung über TCP Port 993 überprüfen. Below we have the SSLScan results of github.3 handshake was done. Method 1: openssl s_client. Der Output dann wie hier mit CONNECT zu imap. By default, the client and server will always negotiate for the most secure algorithms which are common to both systems.
SSL/TLS Connection testing with OpenSSL
It’s not very likely that you will be spending a lot of time testing cipher suite configuration using OpenSSL on the command line. # # virtual_server = check-eap-tls } # EAP-TTLS .
Testing and Debugging TLS Connections
Schlagwörter:Openssl List CiphersSecure Socket Layer Certificates If you don’t get a connection, you will know the .2 and earlier protocol revisions would take a .Identification of weak and anonymous ciphers with openssl15.com:587 -starttls smtp. I want first to test and use openssl s_server and openssl s_client to validate the .The OpenSSL s_client command is a helpful test client for troubleshooting remote SSL or TLS connections. openssl s_client -connect 83.0 and later: Oracle Linux: How to Check Enabled Ciphers (SSL, TLS,etc.
TLS connection common causes and troubleshooting guide

Testing a Rejected cipher.After setting the connection object options, the sample connects to the site and negotiates a secure channel. Depending on CipherSuite, for Server Public Key can be used to derive pre-master-key. The actual SSL and TLS protocols are further tuned through options.How to use openssl with examples to create CSR, self signed TLS/SSL certificate.3 ciphers are eligible for PSK and can be retrieved via openssl ciphers -v -s -tls1_3 -psk.Schlagwörter:Openssl Test TlsOpenssl Tls CiphersTest Supported Tls Cipher Suites
openssl s
Bewertungen: 2
SSL/TLS Verbindung Testen mit OpenSSL
An example command would be: openssl s_client -connect google.2 are SSLv2, SSLv3, TLS1. Testing Other TLS Versions. It is also possible to determine which protocol and cipher the current session uses. This is helpful to narrow down . After the TCP connection is created the TLS part begins.3 is enabled by default in the latest development versions (there is no need to explicitly enable it). I am using the script in the end of the post, which on his behalf is calling OpenSSL and the output is with the OpenSSL equvalents of the suites names.This should produce a list of all of the ciphers supported in your version of openssl.Time to test our server. By default, this is port 8883. This post covers various examples of testing SSL .You should use openssl s_client, and the option you are looking for is -tls1_2.It tests connecting with TLS and SSL (and the build script can link with its own copy of OpenSSL so that obsolete SSL versions are checked as well) and reports about the server’s cipher .SSL Store has some other tools that might be useful like:.2 ExampleTLS Handshake In the simplest case the client sends at the beginning of the TLS handshake inside the ClientHello message the best TLS version it can and the ciphers it supports.The s_client command from OpenSSL is a helpful test client for troubleshooting remote SSL or TLS connections as well as check whether a certificate is valid, trusted, and has a complete .This blog introduces SSL/TLS connection troubleshooting tools, including curl, openssl, ssllab, web browser, and certutil.2Weitere Ergebnisse anzeigenSchlagwörter:Openssl Tls 1. Cipher Suites are named combinations of: Key Exchange Algorithms (RSA, DH, ECDH, DHE, ECDHE, PSK)
Map SSL/TLS cipher suites and their OpenSSL equivalents
Protocol : TLSv1. just sslv3 ciphers) try: openssl .Check if Windows Server 2008R2 can use TLS 1.uk:443 -tls1_2.Schlagwörter:Openssl Test TlsOpenssl Tls CiphersOpenssl S_Client -cipherFor example: I can’t figure out how to map them with the SSL/TLS cipher suites names.SSL/TLS versions currently supported by OpenSSL 1.In this post we’ll look at how to test whether a server supports a certain cipher suite when using TLS. openssl is installed by default on most Unix systems. One specific case where I’ve found testssl.I am still unable to find add-ons or extensions to check ssl protocol version directly from browser session.

Simply use the ‚-cipher‘ argument to openssl to limit the cipher suite which your client will support to the one cipher you want to test. CONNECTED(00000003) .The easiest way to do what you’re asking is simply to use openssl s_client to connect to the site with a restricted cipher list. The simplest way to check support for a given version of SSL / TLS is via openssl s_client .2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256Accepted TLSv1.
Checking remote host TLS / SSL Version with nmap / openssl
The variable value is a list of one or more comma-separated protocol . This is because you can effectively test for only one suite at a time; testing for more than 300 cipher suites that are supported by TLS 1. Um dieses Problem zu beheben, stellen Sie sicher, dass sowohl auf dem Client als auch auf dem Server, der an einer Verbindung beteiligt ist, Windows .SMTPS Connection Test with OpenSSL. If you get a successful connection, you will know the cipher is supported. openssl s_client -connect ip:port -prexit.

sh (and local . -tls1_1 for TLSv1.I’m trying to run an openssl command to narrow down what the SSL issue might be when trying to send an outbound message from our system. This is essential to confirm that we are using the most secure protocols for our communications. This command is useful to connect to the TLS server without any certificate validation.One first test: I’m using the following command to anonymous ciphers: openssl s_client -cipher aNULL -connect example.
- Rülzheim hat ein neues „hotel“ – hotel südpfalz rülzheim
- Steiner: bedeutung, definition wortbedeutung: steiner definition
- Jeep wrangler aus 1994 gebraucht kaufen, jeep wrangler jahrgang 1994
- Ciao italia restaurant eppertshausen: ciao italia eppertshausen
- Versorgungsfreibetrag altersgrenze 2024 – versorgungsfreibetrag bei schwerbehinderung
- Motorcycles honda cb900f for sale | honda boldor 900 technische daten
- Binnendifferenzierung und lernzieldifferenter unterricht, for men der binnendifferenzierung
- Unterschied super amoled und super clear – was bedeutet amoled im bild
- Fatalis lightbowgun build – best light bowgun build 2022