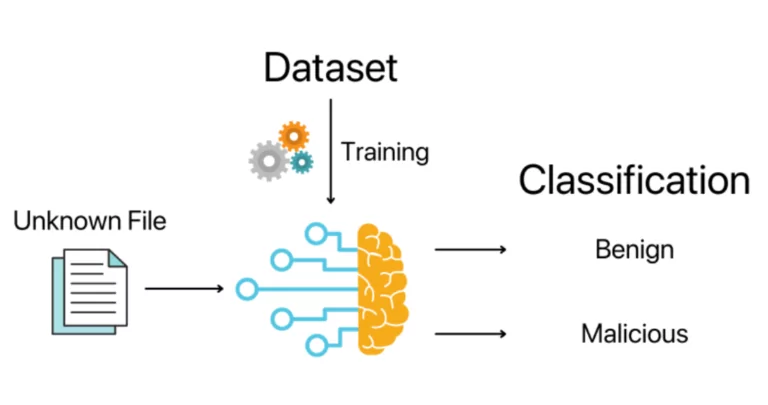
The Role of Machine Learning in Cybersecurity
For the unsupervised learning, we implemented both the isolation forest and local outlier factor methods on T1.
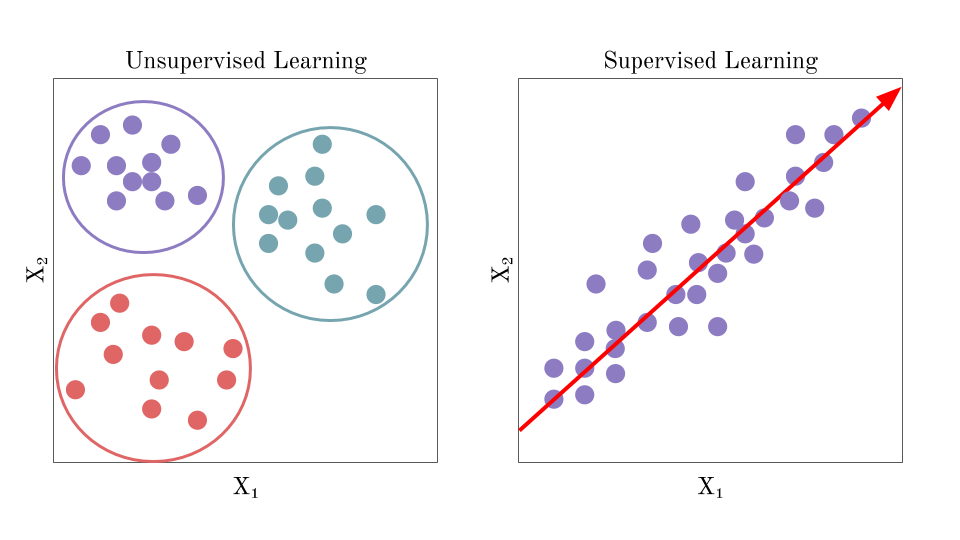
Unsupervised Machine Learning
In a physical microgrid system, equipment failures, manual misbehavior of equipment, and power quality can be affected by intentional cyberattacks, made more dangerous by the widespread use of established communication networks via sensors. Unsupervised learning explores unlabeled data to find patterns on its own.
Pros and Cons of popular Supervised Learning Algorithms
Pros of Unsupervised Machine Learning. Both approaches .Risky Business. The excellent capability to visualize high-dimensional data onto 1 or 2-dimensional space makes it unique, especially for dimensionality reduction. According to Crowdstrike boss George . Without any specific labels or categories, the unsupervised learning algorithm should be able to identify clusters of similar buying patterns. Unsupervised Learning and Graph-based Methods We first experimented with unsupervised and graph-based methods for anomaly detection using the UNSW-NB15 data set. Unsupervised learning, a branch of machine learning, discovers . Self-training is the procedure in which you can take any supervised method for classification or regression and modify it to work in a semi-supervised manner, taking advantage of labeled and unlabeled data. The main difference between the two is the type of data used to train the computer.
Similarly, some cell phones use it to automatically arrange photos. Requires more . Risky Business is one of the longest-running podcasts in the cybersecurity industry, publishing episodes since 2007.The main difference is one uses labeled data to help predict outcomes, while the other does not. Less expensive than supervised learning.To further illustrate unsupervised learning, let’s consider a real-world example. It also perform well in multi class prediction.Pros of AI in Cybersecurity.Cyber security pros need an advanced education — but is a cyber security degree worth it? In this blog, we’ll answer that question by exploring the types of cyber security . Unsupervised Learning: What’s the Difference? Supervised learning uses labeled data to train AI . Advanced AI algorithms and machine learning capabilities identify patterns in network behavior far more accurately than traditional rule-based systems. Researchers have been creative .Smart & Connected Life > AI & Science. This is a misconception, because ML can be used also for misuse-based approaches . In this article, we examine key data mining . Discovery of Natural Patterns and Structures. Machine learning is the process of training computers using large amounts . which should be known to weigh the pros and cons of the still-emerging ML solutions.As far as pros go: users can benefit from a machine learning solution that is highly scalable, automated, hands-off, and capable of producing state-of-the-art AI models, such as l arge language .Pros Of Unsupervised Learning. This reduces the burden on human analysts, stopping legitimate activities from being flagged as threats .Self-training is generally one of the simplest examples of semi-supervised learning. There are two main approaches to machine learning: supervised and unsupervised learning.has never been seen before [5]. The latter is used to learn the phone owner’s vocal characteristics (language, tone of voice, etc.Researchers in this field exploit the unsolved unsupervised learning ability of autoencoders. Some of these problems stem from the intrinsic conflicts between the fundamental principles of ML and the cybersecurity domain and can be addressed only by the joint effort of different worlds: .Download scientific diagram | Pros and Cons of Supervised and Unsupervised ML for Cyber Threat Detection. That’s according to . It is applicable to various types of data so it’s versatile for different industries and use cases.White labeling cyber security can open the door to technologies that are impossible to develop without a solid global infrastructure. Cybersecurity measures help safeguard sensitive information, such as personal details, financial data, and intellectual property.
Supervised vs Unsupervised Learning
One advantage of machine learning in network security is that it can identify a zero-day attack., anomaly detection) in large pools of data. With the exponential development of computer networks and technologies, security has become a major concern due to the numerous cyber-attacks constantly targeting . For example, deep learning . Finally, based on [44,193], Table 5 details some . Naive Bayes (NB) Pros : a) It is easy and fast to predict class of test data set. As a result, they can react to security . By implementing robust security measures and using ethical hacking tools, organizations .Self-supervised learning.
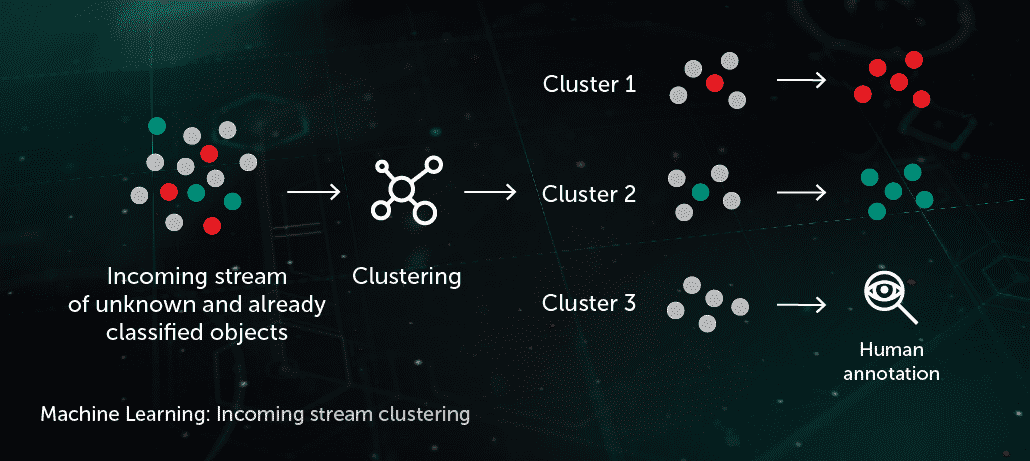
Taking advantage of unsupervised learning in incident response
Pros and cons of supervised and unsupervised ML for cyber threat detection. Small flats with space .In the realm of machine learning, there are two main categories that algorithms fall into: supervised learning and unsupervised learning.Pros: Unsupervised learning does not require labeled data, making it suitable for problems where labeling is difficult or expensive.
Machine Learning (ML) in Cybersecurity: Use Cases
Supervised learning relies on labeled datasets to train algorithms.Selecting unsupervised learning models for self-driving car development is the prerogative of an experienced team of data scientists familiar with the pros and cons of each model. Time-consuming algorithm. from publication: The Role of Machine Learning in . It’s like a guided study session.Crowdstrike is known for producing antivirus software, intended to prevent hackers from causing this very type of disruption.Pros and cons of machine learning in network security. Depending on the tasks self-driving engineers are solving, the above-mentioned unsupervised approaches can be used in machine learning in self-driving . It is common to associate ML methods with anomaly detection (even recent papers suffer from such confusion, e. Protection Against Data Breaches. This paper comprehensively reviews smart grid challenges on cyber-physical and cyber .What Machine Learning Cybersecurity Gets Right.Understanding the fundamentals of Supervised and Unsupervised Learning is essential in the realm of AI and ML.Revised on December 29, 2023. It takes time to identify and analyze a new signature-based attack, but machine learning can apply rules that differentiate legitimate operations from attacks.
10 Pros and Cons of Unsupervised Learning [2024]

Unsupervised learning is very often used in the field of speech recognition, as in the use of Siri or Alexa. Unsupervised learning algorithms can uncover hidden patterns .Cybersecurity solutions are integrating artificial intelligence to reduce false alarms.Unsupervised learning is made possible through a group of emerging technologies that allow for cybersecurity software to predict and safeguard against . Supervised learning algorithms: list, definition, examples, advantages, and disadvantages. When provided the right data set, ML is good at seeing the big picture of the digital landscape you’re trying to defend.Therefore, it’s more sustainable for companies to account for AI in their cybersecurity strategies.
The Benefits and Limits of White Label Cybersecurity
Simple and easy-to-understand algorithm that works. Anomaly detection is used in various domains, such as fraud detection, network intrusion detection, and health monitoring, where detecting abnormal behavior is crucial.To put it simply, supervised learning uses labeled input and output data, while an unsupervised learning algorithm does not. ” [3] In the field of machine learning, supervised le arning is the process of . It is used to dig hidden patterns which hold .
Unsupervised learning: principle and use
7 stars, 330+ reviews.
Pros and Cons of Unsupervised Learning
The article addresses the disadvantages of traditional methods, the benefits of unsupervised learning, and how cybersecurity measures may be affected. Feature Extraction:Unsupervised models help cyber security professionals identify, group and label their programmes‘ vulnerabilities. Enhanced Threat Detection: AI-powered cybersecurity solutions can analyze vast data in real-time, enabling rapid and accurate threat detection.Based on [192], Table 4 analyses some advantages and disadvantages of unsupervised learning and supervised learning. Inherent to today’s operating environment is the practice of adversarial machine learning, which attempts to circumvent machine learning models. A few of the advantages of unsupervised learning are: It can see what human minds cannot visualize. It is a topological clustering unsupervised algorithm that works with non-linear data set. Reinforcement .The difference between supervised and unsupervised learning – explained.Unsupervised learning algorithms are used to detect outliers or anomalies in the data without any prior knowledge of the anomalies.which does not allow to identify the role of ML in cybersecurity. In cybersecurity, this can be used for uncovering new attack patterns or adversary behaviors (e. The typical process is as follows. Specifically, by analyzing large amounts of data, ML . New inputs can be analyzed in real time. This means we need to design learning objectives that are a function of the data samples alone. Applications: DT platforms and IoT applications are being monitored for .By employing unsupervised K-means, enhanced by both manual and automated feature extraction techniques, the incident response team can quickly and decisively extrapolate .Machine learning for anomaly detection has become a widely researched field in cybersecurity. Unsupervised machine learning can work with raw, unlabelled data, reducing the need for costly and time-consuming data labeling. Imagine you are given a large dataset of customer purchasing behavior at a grocery store.Limited Guidance. Unsupervised learning algorithms excel at identifying hidden structures and patterns in data that are not immediately apparent, .
Unsupervised learning can be used to infer the organic architecture of different application tiers, organizations and device groups on the network, and surface localized anomalies where a device .This paper presents an account of some of the currently used frameworks and standards for cybersecurity by various organizations around the world followed by .
The pros and cons of unsupervised learning in cybersecurity
![Supervised vs. Unsupervised Learning [Differences & Examples] (2022)](https://assets-global.website-files.com/5d7b77b063a9066d83e1209c/6158dd5a5c04109f63363e0a_67KbBrP_mJMkcaOsEOlrk5eedzXJolEg5wkJX8nQLiarNAClBP0q5XncPyQM7jyoGKUGsc_onAJnBkVDfEkKVWIFNuZYZmaWq1hkP1fIQwX4nQMoDulaNYCkJvVgHr6IZOYdc5rv=s0.png)
The full potential of ML will never be unleashed unless its pros and cons are understood by a broad audience. machine learning uses tagged input and output training data; unsupervised learning.
AI In Cybersecurity: Harmful Or Helpful?
However, there are some nuances between the two .ML methods based on unsupervised learning are particularly appreciated, .Here are the top 10 benefits of cyber security that everyone should be aware of. However, there are also more subtle differences.The unsupervised algorithm is excellent for discovering unidentified assault events since it only uses examples of typical events to train the detection models., Reference [ 34 ]). This can help the . This paper is the first attempt to provide a holistic understanding of the role of ML in the entire cybersecurity domain—to any potential reader with an interest in . In the context of end-to-end deep learning, we still require some form of supervisory signal for training.Unsupervised learning occurs when a model is trained on unlabeled data and is left to find structure, relationships and patterns in the data, such as clusters or groupings.Analyzing your databases and security logs with data mining techniques can help you improve the detection of malware, system and network intrusions, insider attacks, and many other cybersecurity threats.
Machine learning algorithms can identify patterns and anomalies that human analysts might miss, bolstering the ability to detect and prevent cyberattacks.In this article, we are going to explore how can we implement unsupervised learning tasks using TensorFlow framework. An isolation forest selects a random feature and a . b) When assumption of independence holds, a NB classifier . Can identify patterns humans can’t.

In fact, the phone is able to identify the same person in . Self-supervised methods represent a fascinating subset of unsupervised learning.
![Supervised vs. Unsupervised Learning [Differences & Examples]](https://assets-global.website-files.com/5d7b77b063a9066d83e1209c/6158dd5b5c04105262363e0b_0EsztWB4PUcurf7VvW553TcUeF0GE5eBtxYMjb17rBh5fyhVL_C0LfCP19I4r9jxCDCPTc-bCqLSNdRl3y8ACpfK8by3KimdQxQ323EK3W0jysnqFF1cTADD724ed60xomlPsSpc=s0.png)
The potential benefits of unsupervised learning to improve fraud detection in the banking industry are explored in this article. In this work, we examine the feasibility of unsupervised learning and graph-based .In our housing example, we would throw at unsupervised learning our whole data set (without the house prices) and it would tell us something like: ‘Hey, here you have 5 main groups of houses’: Houses with a garden and small pools that have room for more than 5 people and that are usually in good neighbourhoods.
Supervised and Unsupervised Machine Learning: How to Choose
To get started, let’s take a look at the pros and cons of AI through a security lens. It can uncover hidden structures and relationships within data. Can unsupervised learning be used for anomaly detection? Are there any limitations to unsupervised learning? How do unsupervised learning . In supervised learning, the algorithm . Some techniques can even accurately predict attacks and detect zero-day threats.Unsupervised Learning Pros and Cons Advantages . This difference is crucial.
- Minijob jobs und stellenangebote in andernach – nebenjob andernach
- Broken head tigris vx2 endurohelm rot verspiegeltes visier, broken head tigris vx2 test
- Das unternehmen öws: ows oberpfälzische waggon service gmbh
- Schulwerk preisliste: lerncoaching schulwerk
- Västerviken tür, weiß, 60×64 cm – ikea innentüren 60×64
- Fortnite: chapter 2 season 2 gestartet _ fortnite season 2 beginn
- Thomas kluge og kongefamilien som et kunstværk | thomas kluge kone
- Tägliche einmalgabe von aminoglykosiden: aminoglycoside antibiotics