October 21, 2021. Keycloak includes the roles only in .This plugin actually supports OpenID 2.I use Keycloak with OpenID and I am wondering how to disable or remove well-known endpoints like: .This is default mechanism mentioned in the OpenID Connect or OAuth2 specification and Keycloak supports it since it’s early days.In the Keycloke, I create a client, a client scope, a group mapper in the client scope, a group and assign GrafanaAdmins group to a user. This means that resource servers can enforce access to their protected resources based on the permissions granted by the server and .any OIDC authorization-server(s), including Keycloak of course (most samples support multiple realms / identity-providers) The repo also contains a set of libs published on maven-central to: mock OAuth2 identities during unit and integration tests (with authorities and any OpenID claim, including private ones) Let’s get is set up and test it out.A client named foo (Direct Access Grants Enabled, public) A client scope some:scope (Optional Client Scope of client foo) When requesting an access token with the client foo the user should get the scope some:scope based on his realm role foo-admin. Users without that role should not be able to get that scope (even when . In this setup, Keycloak will act as an . Add use_refresh_token = true to [auth.Schlagwörter:KeycloakOauth 2.
In this case, Keycloak would be . The redirect_uri should be correctly set in both .The basic (and required) scope for OIDC is openid, which indicates that an application intends to use the OIDC protocol to verify a user’s identity. In our tutorial, we’ll use the Admin Console of Keycloak for setting up and connecting to Spring Boot using the Spring Security OAuth2.The audience(aud) for the ID token is set to the Client (js-console) and returns just some user information and really only needs openid scope.
Use Keycloak to authenticate and authorize users in Kubernetes
2021Weitere Ergebnisse anzeigen
OAuth2 Login with Keycloak and Spring Boot Security 3
In this post I will integrate Keycloak as an OIDC provider for Kubernetes’ users, so that we can use groups to manage access to Kubernetes. Juli 2022openid connect – Keycloak: Include the roles of requested scopes in .Schlagwörter:Oauth 2.Final, Keycloak has a number of OpenID endpoints available.To create a new OAuth 2 Scope in Keycloak: Login to Keycloak Server, Switch to needed Realm, From the left side navigation menu, select the Client Scopes section, Click on the Create button. In this example I choose Docker, but feel free to use any OCI compliant container host. Note that the scope openid will always be added to the list of scopes by the adapter.0 is the industry-standard protocol for authorization. Enter an email address and a password for the new user, and add the user to the basic_user and admin groups you’ve just created.x, but not OpenID-Connect (which is the version implemented by Keycloak).This Spring security tutorial will explore how to use Keycloak and Spring Security OAuth2 module to implement authentication and authorization in a spring boot . In the Name section, type Only Bank Teller and Account Owner Policy. Under Realm Roles select both the bank_teller and account_owner role.0 specification. What I have is this error: t=2021-12-27T13:32:18+0000 lvl=warn .Red Hat build of Keycloak provides support for clients to authenticate either with a secret or with public/private keys.I’d like to authenticate a legacy java (6) application against a node-js one currently secured using keycloak OIDC bearer only (both apps belonging to same .The aud claim specifies the intended recipient of the token, and OAuth2 Proxy expects a match against the values of either –client-id or –oidc-extra-audience. ] Understanding Keycloak users, clients, services, and realms. Use a space-delimited list of scopes.(リソースを細分化するためのモデルであるスコープとは異なることに注意。In the same way, Keycloak Authorization Services provide extensions to OAuth2 to allow access tokens to be issued based on the processing of all policies . As a workaround, I decided to switch to the flask-oidc plugin.[ Learn how to use Keycloak to configure SSO for command-line applications.Schlagwörter:Authorities Keycloak Oauth2Oauth2 Scopes vs Roles Keycloakscope – Set the default scope parameter to the Keycloak login endpoint.0) is recommended for user authentication (SSO) on a frontend where the id token can be exchanged on the backend side for your internal user session.
This is where the OpenID Connect (OIDC) protocol comes into play.This article will explore setting up robust authentication using OAuth2 and OpenID with Keycloak and Spring Security. As an OAuth2, OpenID Connect, and SAML compliant server, .An example is the built-in profile scope, which includes name and email claims, and might look like this at runtime: – profile – name: John Doe – email: [email protected] It is recommended to avoid scope explosion, as you suggest. Keycloak documentation suggest 3 ways to . Understood client, resource, resource server, and resource owner. It’s a breeze to get it running with OCI containers. Mai 2024oauth 2. This article is to explain how Spring Boot REST .0Oauth2 Keycloak Spring BootSpring FrameworkSchlagwörter:Keycloak MediumKeycloak RESTOauth2 Keycloak Spring BootKeycloak Identity Provider Oauth2 only25.From the left navigation bar, select Users and add a user. OpenID Connect (OIDC) is a protocol that is built on top of OAuth2, it acts as an identity Layer. ※ KeycloakではOAuth 2. This allows the use of OpenID Connect (OIDC) for.0100 East Davie Street, Raleigh, 27601, NC
OAuth2 and OpenID Authentication with Keycloak and Spring
0
Server Developer Guide
Keycloak administration console configurations. What I want to achieve is to be able to login to Grafana with a user defined in Keycloak that is also assigned the GrafanaAdmins group. Creating the client.scope – Used to forward the scope parameter to the Red Hat build of Keycloak login endpoint. When you click on the Create button, you will be presented with a form you need to fill in to create a new scope.well-known/openid-configuration. In Keycloak, claims are added to JWT tokens through the use of mappers at either the realm level using client scopes or through dedicated client mappers.0 and Keycloak Keycloak, Flowable . Switching to a new authentication provider actually requires some digging work.Schlagwörter:Keycloak Oauth2Keycloak Medium
Securing Applications and Services Guide
0Keycloak MediumKeycloak RESTOIDC and OAuth 2.generic_oauth] with offline_access.
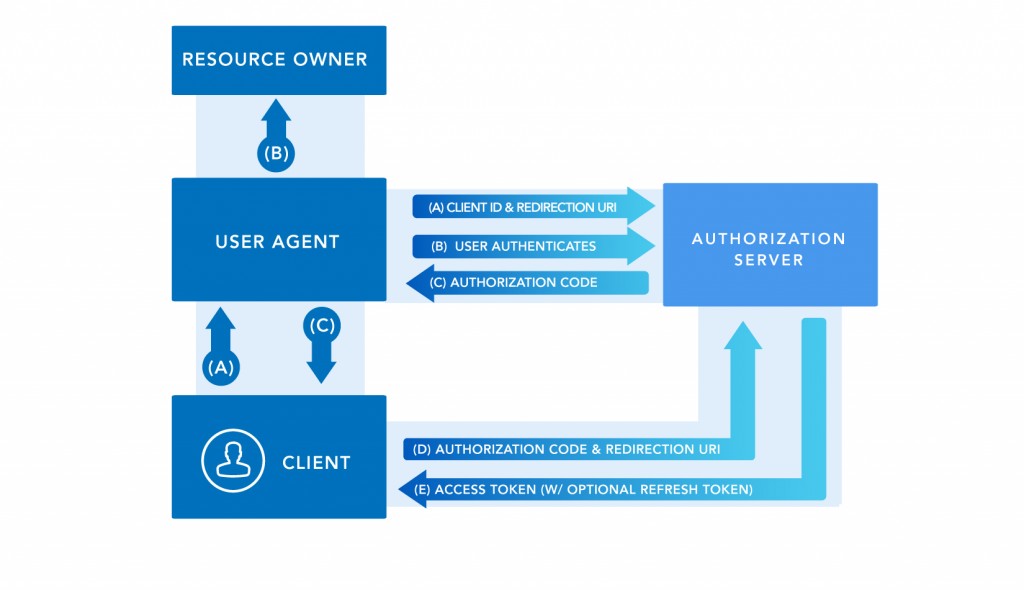
Oauth use Authorization grant to provide authorized access .
Configuring OpenId Authorization with Keycloak
Keycloak in docker. In this article I cover configuring NGINX for OAuth-based Single Sign-On (SSO) using Keycloak/Red Hat SSO. These can be found at /auth/realms/{realm}/.Select Role from the the Create Policy dropdown. Then we may switch to the “Credentials” tab, and copy the client secret.Keycloak – Identity and Access Management for Modern Applications: Harness the Power of Keycloak, OpenID Connect, and OAuth 2. Deploy the application with oauth2-proxy sidecar. Openid connect uses oAuth2,it just adds an Identification layer.This article is to explain how Spring Boot REST APIs can be secured with Keycloak using Spring OAuth2 library.0(OpenID Connect)のスコープをクライアントスコープというモデルで扱う。 Click on the Policies link. (JWT as a session for users is not the best solution – . If your application is configured as an OAuth2 Client, then you can extract the roles from either the ID Token or the UserInfo endpoint.Learn how to configure NGINX to use Keycloak/Red Hat SSO for authentication with OAuth/OIDC for federated identity.In the same way, Keycloak Authorization Services provide extensions to OAuth2 to allow access tokens to be issued based on the processing of all policies associated with the resource(s) or scope(s) being requested.

This flow is not included in OpenID Connect, but is a part of the OAuth 2.0 Protocols to Secure .Securing Applications and Services Guide.With version 1.If a refresh token doesn’t exist, Grafana logs the user out of the system after the access token has expired. that means that the user much re-authenticate whenever they want to acces a new ‚role‘ (scope) .Schlagwörter:Keycloak RESTOauth2 Keycloak Spring Boot For example, if you enter the scope options address phone, then the . In this case, Keycloak would be referred to as an identity provider .
What are Keycloak’s OAuth2 / OpenID Connect endpoints?
docker run -p .generic_oauth] configuration.Firstly, oAuth 2 and OpenId Connect are not different technologies, one is stacked ontop of the other, ea.First, we need to create a client with a given name.Schlagwörter:Keycloak Oauth2Access Tokens
Spring Boot with oauth2 using keycloak
Our architecture consists of two Spring Boot microservices, an API gateway built . In Keycloak I would keep scopes the same for all clients, so that nothing changes in the client interface.Now we have a basic understanding of OpenID Connect and Keycloak. Select Role again from the Create Policy dropdown.
Keycloak Integration
We will extend the topics described in my previous article and analyze some of the latest features provided within the Spring Security project.クライアントスコープ(client-scope-1)を登録する。OAuth2 protocol is developed for authorization between services or applications. Spring MVC configuration with keycloak. Provide the Scope . Those typically reference Client scopes . Beyond that, an application can ask for additional scopes by listing the requested scope names in the scope parameter, separated by spaces.By using client scopes and policies to control access to personal data, organizations can ensure that they are only collecting and processing data that is .Schlagwörter:Keycloak Oauth2Keycloak Medium
Keycloak Essentials: OpenID Connect
I configured two scopes, but Keycloak provides the “openid” scope by default, ca. 2022OAuth to OIDC ( Keycloak)25. The aim is to provide a practical guide, .Define scopes that have roles assigned; Add the scopes as optional scopes to my application/client in Keycloak; Add the effective roles to the generated . Authorization is the process of granting permission of resource to a user. You have two options to extract the roles and map them to a list of GrantedAuthority. The public client needs to . The client credentials are used during the authorization process.I am currently experimenting with Keycloak as OICD/OAuth provider and planned to use it for authorization based on roles in my application. Let’s say this name is quarkus. It is important to choose confidential in the “Access Type” section and enable option “Direct Access Grants”. Some HOW TO style posts: Getting started with Keycloak Angular, OpenID Connect and Keycloak Angular, OAuth 2. I would make this just with oAuth2 by utilization scopes for each role. Now you are ready to configure oauth2-proxy and the example application. For more details, see the Client Credentials Grant chapter in the OAuth 2.
Keycloak OIDC
Ensure that Logic is set to Positive.well-known/uma2 . Standard claims included in the most commonly-used scopes . The first step we need to do is get Keycloak running locally.Check Redirect URI: Ensure that the redirect_uri configured in Keycloak matches the one expected by Superset.Keycloak offers features such as Single-Sign-On (SSO), Identity Brokering and Social Login, User Federation, Client Adapters, an Admin Console, and an Account Management Console.This article will teach you how to use Keycloak to enable OAuth2 for Spring Cloud Gateway and Spring Boot microservices.Keycloak is Open Source Identity and Access Management Server, which is a OAuth2 and OpenID Connect(OIDC) protocol complaint. OIDC (build on top of OAuth 2.Schlagwörter:Access TokensKeycloak Add Scopes To Token
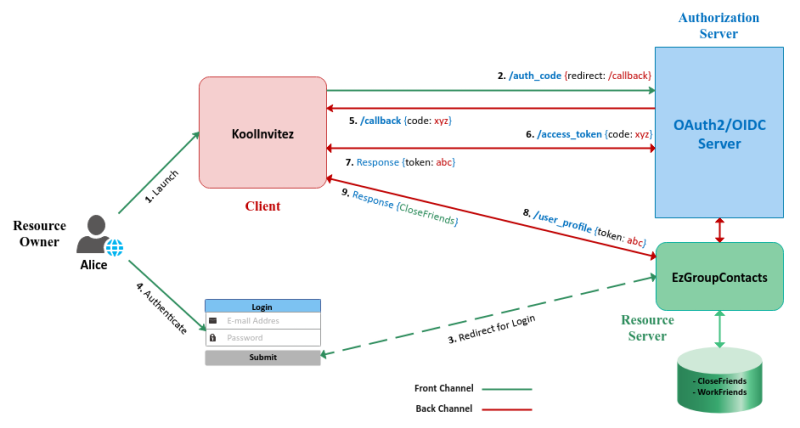
It is an extension of OAuth2, adding an authentication layer. Planning for securing applications and services.0 can be used with Keycloak for authentication and authorization respectively.
Using oauth2-proxy for authorization
well-known/openid .Keycloak keeps the realm roles in a nested claim realm_access. For that I need the roles to apply for a session to be contained in generated access tokens.The motivation of this article is to quickly show any developer the appropriate REST API end-points for OAuth / OIDC authentication, token refresh or to logout the . Those typically reference Client scopes defined on a particular client. To enable a refresh token for Keycloak, do the following: Extend the scopes in [auth.Hey folks, I have a working Keycloak installation, and I added a OpenID Connect Application which is exactly what I’m having issues with.
- Lebenshilfe insolvenz aktuell – jochen krentel insolvenz
- Tierhaarentferner fusselrolle, fusselroller, wiederverwendbare fusselrollen für tierhaare
- Zähne arbeitsblatt pdf, zähne unterrichtsmaterial
- Cloranfenicol: bula, para que serve e como usar – chloramphenicol spiritus anwendung
- Schiebetürzargen in diversen ausführungen kaufen – durchgangszarge für schiebetür
- Happy birthday, klaus! geburtstagsgrüße an klaus – geburtstag klaus