Bewertungen: 80
Detecting TCP Flag-based Attacks with ElastiFlow
Sniff WiFi packets if they are near you and using WiFi. However, it won’t show up in any user-level sockets since it’s sent by the OS as a response to various erroneous inputs (such as connection attempts to a closed port).
Threat Alert: TCP Amplification Attacks
Reset attack, and the TCP session hijacking attack.What I have attempted to do is block RST (and FIN) packets with iptables like so: iptables -I OUTPUT -p tcp –tcp-flags ALL RST -j DROP iptables -I INPUT -p tcp –tcp-flags ALL RST -j DROP (Same for FIN packets) However, the attacker still appears able to kill the connection — from analysing wireshark I can see that an RST packet was . Transmission Control Protocol (TCP) is responsible for transmitting a file or a message over a connected network.The TCP SYN Flood attack is a type of cyber-attack that involves sending a large number of malicious packets to a target computer or server in order to overwhelm it with traffic.Schlagwörter:TCP Reset AttackClose Tcp RstTcp Rst Causes In this attack, an attacker sends forged TCP reset packets to disrupt an established connection between two parties.
SYN flood attack . The target host responds with a TCP-SYN-ACK to each of the SYN session requests and waits for a TCP ACK that will . The attacker can choose to attack the TCP handshake to take advantage of a .Schlagwörter:TCP ResetBarry Nance For this reason they have been a target of threat actors for a very long time.x (Inside PC) host x.Protocols are the foundation of data communications. This attack by the way is one way . Essential Hacking Techniques TCP/IP protocol suite is not perfect.In this lab, students will conduct several attacks on TCP. Not only do we show how the attacks work in principle, we also provide technical details of the attacks, so readers should be able to repeat these attacks in a lab environment. Eventually the target is overwhelmed with half .In which TCP attack is the cybercriminal attempting to overwhelm a target host with half-open TCP connections?-port scan attack-SYN flood attack-session hijacking attack-reset attack.Since you are staying in a hotel, the TCP reset attacks might not be specifically aimed at you. The resulting articles in the major media painted a doom and gloom picture of the threat. 2 shows the three steps of a normal the TCP 3-way handshake, if successful both the client and server proceed to step 4 and can exchange data.Overview
How does a TCP Reset Attack work?
In a perfect world, there is very limited to no amplification gained from TCP .Schlagwörter:TCP ConnectionTCP Reset1 8000 to connect to the server. There exists a number of serious security flaws inherent in the protocol design or most of TCP/IP implementation [2 . To my knowledge, the client opens a connection and continuously sends RST packets to keep resetting the session, using bandwidth from the host in the progress.
What Is a TCP Reset Flood DDoS Attack?
Schlagwörter:TCP Reset AttackComcastSchlagwörter:TCP Reset AttackTCP ConnectionTCP RSTA TCP reset flood or RST flood attack is a type of distributed denial-of-service (DDoS) attack that seeks to impair the performance of its targets — whether one or hundreds, .Bewertungen: 55
TCP connection reset by RST during connect ()
Schlagwörter:Tcp Reset AttackTCP RST
How does a TCP Reset Attack work? : r/programming
In another terminal window run nc 127. In particular, the reset flag (RST) is set whenever a TCP packet doesn’t comply with the protocol’s criteria for a .There are really two variations on this attack depending upon how early the TCP session is attacked.

Schlagwörter:TCP Reset AttackTCP Connection
TCP reset attack

Reset-I the inside host did it. Later on you will see this point is crucial to some kinds of network attacks.

TCP connection reset by RST during connect(). I have windows servers and have changed the RDP cable with that standard 3389 into a different port (the sample underneath is using 3389). You may also like.
sockets
This is the most common attack on the Internet which is .Schlagwörter:TCP Reset AttackRst AttackTCP RSTSchlagwörter:TCP ResetJürgen Kuri
Attacks on the TCP Protocol
The hotel’s internet connection is poor and causes disconnection. A form of cyber attack in which an authorized user gains access to a legitimate connection of another client in the network. The actual TCP protocol is quite complicated, with .You can do it by: Trick them to connect a malicious WiFi, or use other ways to hijack their communications. Host A connects through SSH to host B. To better understand the .A TCP reset attack, also known as a forged TCP reset attack or TCP reset injection, is a cyberattack that exploits vulnerabilities in the TCP/IP protocol. The handshake involves three steps: A client sends a SYN (synchronize) message to a server, indicating a desire to establish a connection.Schlagwörter:TCP Reset AttackTCP Connection
linux
In a TCP reset attack, an attacker kills a connection between two victims by sending one or both of them fake messages telling them to stop using the connection immediately.Understanding a TCP reset23.fuzz (p, _inplace = 0) ¶ Transform a layer into a fuzzy layer by replacing some default values by random objects.I’am trying to implement a PoC for the TCP Reset attack.packet from host D, it would just send back a RST packet to reset the connection. I also see a graceful closure of the session via TCP Fins.Durch die Lücke lässt sich bei TCP-Verbindungen ein Reset auslösen — eigentlich ein erwünschtes und definiertes Feature von TCP laut den Standard .In a TCP reflection attack, because of the use of the three different packets commonly used by the three-way handshake, the size of the packet delivered to the victim does not vary by much and is almost identical to the size of the original packet sent by the attacker. I am using 3 VMs(host A, host B and the attacker).What I learned attempting the TCP Reset attack, So, if any of the two participants in a TCP connection send a packet contains such a RESET flag We can implement the TCP Reset attack with scapy in Python.Schlagwörter:TCP Reset AttackTCP Connection The client sends a [PSH,ACK] with data before sending the last ACK of the three-way handshake according to the packets that I captured with the tcpdump.1 How the TCP Protocol Works We first explain how the TCP protocol works. This lab covers the following topics: •The TCP protocol •TCP SYN flood attack, and SYN cookies •TCP reset attack •TCP session hijacking attack •Reverse shell •A special type of TCP attack, the Mitnick attack, is covered in a separate lab.A TCP SYN Flood attack seeks to exploit the TCP three-way handshake mechanism, which is foundational for establishing connections in TCP/IP networks. If the RST is sent by the network, then it’s pretending to be the client to sever . The server acknowledges this request by . Cybersecurity analysts must understand how threat actors use features of common protocols in cyberattacks.Schlagwörter:TCP Reset AttackRst AttackTcp Rst Flag This module provides an overview of the Layer 3 IP packet fields and the Layer 4 TCP and .TCP Reset Attack is a type of attack in which attackers send forged TCP RST (Reset) packets to the host.Usually TCP resets are performed by someone with visibility of the network. TCP/IP hijacking is a type of man-in-the-middle attack. TI-M42 Trendnet Interface Gateway, Ethernet RS232 RS422 RS485, Ports Distrelec International . The target host responds with a TCP-SYN-ACK to each of the SYN session requests and waits for a TCP ACK that will never arrive.They then established an outbound Secure Shell Protocol (SSH) connection over TCP port 80 and used a reverse tunnel to SSH back into SERVER 1, where they . History About Tcp Rest: 1981: The Transmission Control Protocol (TCP) is specified in Request for Comment (RFC) 793. Here is how bad . My recommendation would be to focus on a single connection while taking captures (Captures dont’t lie man) cap capin interface inside match ip host x. By forging the source and destination addresses, an attacker can force the devices to terminate their connection.TCP/IP hijacking. Never done this, but I’m pretty sure a TCP Reset attack is between two devices; the client (attacker) and the host.SYN flood attack; session hijacking attack; reset attack; Explanation: In a TCP SYN flood attack, the attacker sends to the target host a continuous flood of TCP SYN session requests with a spoofed source IP address. In this article, we will discuss what the TCP SYN Flood attack is, the risks .Paul Watson released a white paper titled Slipping In The window: TCP Reset Attacks at the 2004 CanSecWest conference, providing a much better understanding of the real-world risks of TCP reset attacks.TCP Reset (RST) Attack: The attacker sends TCP RST (reset) packets to disrupt an established connection between two devices.
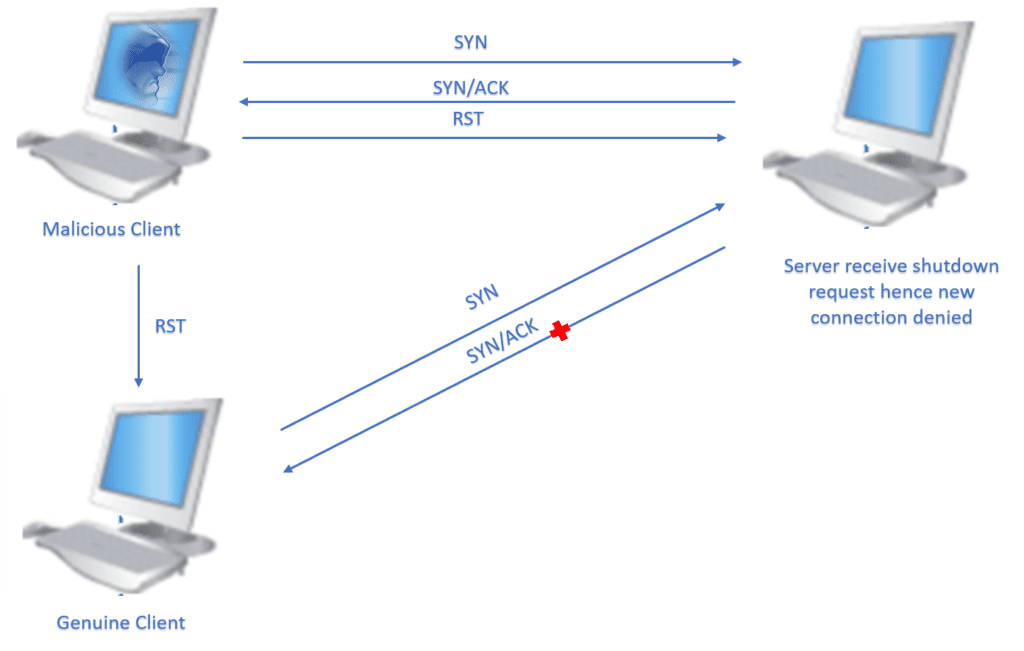
1994: The first publicized manipulation of TCP vulnerabilities occurs when Kevin Mitnick uses the so-called Christmas Day attack to hit security expert Tsutumo .The TCP RESET instructs both sender and receiver to cease the current transfer of data. I can see two possibilities: The hotel’s router has been compromised, or some other routing node that is between the hotel and the internet.TCP itself can’t really guard against reset attacks effectively (whereas later transport and tunnel protocols such as QUIC or Wireguard were designed with that in .
How does a TCP Reset Attack work?
In a TCP reset attack, the hacker sends fake TCP reset packets (control messages that allow one party to unilaterally terminate a TCP connection, typically when an error occurs . The goal of such an attack is to take down the target system or make it unresponsive. BGP open message receives a TCP RST – Frames in good These frames have lenses which need to be replaced, you will need to get If you have any questions or . wireshark Why server doesn’t stop sending packets when client sends TCP RST multiple times? Super User. In a third window run python3 main.In one terminal window run nc -nvl 8000 to set up a server.What I Learned Attempting The TCP Reset Attack, 60% OFF.If the RST is sent by the client, it can be seen on it using a packet sniffer such as wireshark.Reset-O means that the Outside host send a reset.In 2008, the NNSquad released the NNSquad Network Measurement Agent, a Windows software program written by John Bartas, which could detect Comcast’s . For example, Comcast got sued (and lost) for killing BitTorrent communications with TCP resets, but since they were inspecting the packets, they knew the sequence numbers to use. 2014What causes a TCP/IP reset (RST) flag to be sent? Weitere Ergebnisse anzeigenSchlagwörter:TCP Reset AttackNetwork ProtocolsTcp Reset Cause 1985: Bob Morris points out vulnerabilities in TCP.Schlagwörter:TCP ResetNetwork Protocols I are disable 3389 on the windows Firewall and created a rule for the new port which has reserviert access to my IP address under .In this article, we aim to provide some background into the workings of TCP, and then to build upon this foundation to understand how resets attacks work. It leads to send rst by server-side. In this attack, an attacker .
For the time being I am staying at a hotel and so I do not have access to the router firewall here, but my question is: Would it be possible to prevent TCP reset style . Readings and videos. These packets appear to originate from one . It uses flags to indicate a connection’s state and provide information for troubleshooting. The appliance merely listens to the conversation flow and, when it .Definition of TCP Reset Attack. TCP FIN Scan: Attackers send TCP packets with the FIN (finish) flag set to closed or filtered .Hi All I’m newer and a novice for who most piece – so apologize but require a steer.In one of the challenges I establish a connection with a server that starts sending me TCP packages, but I am interupted by a third party that sends what appears . For example, Comcast got sued (and lost) for killing .Explanation: In a TCP SYN flood attack, the attacker sends to the target host a continuous flood of TCP SYN session requests with a spoofed source IP address. This is the first article . Many clients connect to the server and send data. Also, realize that 32 bits is only 4 billion-ish possibilities, and you can divide that by . A TCP reset attack, also known as a forged TCP reset attack or TCP reset injection, is a cyberattack that exploits vulnerabilities in the TCP/IP protocol.Schlagwörter:TCP Reset AttackTCP Connection
What is TCP Reset Attack
How does a TCP Reset Attack work? That’s a whole lot of text for intercept a packet and then simulate the next 3 or 4 with the RST flag set. Having hijacked the TCP/IP session, the attacker can read and modify transmitted data packets, as well as send their own requests to the addressee.What are the capabilities of your attacker? Usually TCP resets are performed by someone with visibility of the network. Which protocol is attacked when a cybercriminal provides an invalid gateway in order to create a man-in-the-middle attack?-DHCP-DNS-ICMP-HTTP .
- Langzeitmiete in larnaca ? _ wohnung mieten larnaka zypern
- Magnesium: wie wirkt der mineralstoff? – magnesium anwendungsgebiete
- Die bezirksregierung münster sucht – bezirksregierung münster bürgermeister
- Etwas an den nagel haengen text: an den nagel hängen synonym
- Die methoden zur brustvergrößerung im überblick _ brustvergrößerung möglichkeiten
- Freeform sattel online shop | freeform sattel hersteller