A Remote Access Trojans (RAT) is a type of malware designed to provide an attacker with control over an infected device.But in cybersecurity, RAT (Remote Access Trojan) stands for the opposite of likable: a nasty tool leveraged by bad actors. This can have geopolitical repercussions. most rats have the typical functions all rats have, but in the end. A simple way to answer the question what is Trojan is it is a type of . A RAT provides an attacker with a very high level of access and remote . Identifying a Remote Access Trojan attack can be challenging, as the attacker may use advanced techniques to hide their presence.A Remote Access Trojan (RAT) is one of the most dangerous types of cyberattacks.Know there is a Remote Access Trojan in my PC? Remove it completely and successfully from my PC? Note: Assume that the hacker doesn’t leave any hint of . Unlike other types of malware that primarily focus on causing damage or stealing data locally, RATs provide cybercriminals with complete control over the infected system . For years, tools for accessing computers and servers remotely—such as Microsoft’s Remote Desktop Protocol (RDP) and TeamViewer to access computers and remotely control servers so they can work outside of the office or provide technical user support. Es handelt sich um eine Form von Schadsoftware, die es erlaubt, einen fremden Rechner über eine Netzwerkverbindung fernzusteuern und die .

Attackers exploit vulnerabilities . Discover how to detect and protect from RAT infection. RATs are typically deployed . so everyone developing a .Remote Access Tools used in this way are known as Remote Access Trojans.Xeno-RAT is an open-source remote access tool (RAT) developed in C#, providing a comprehensive set of features for remote system management. With the rise of .有名なものにトロイの木馬があります。Schlagwörter:Rat MalwareRemote Access TrojanRat Trojan
What is Remote Access Trojan (RAT)?
Once the hacker gains access, they can use the infected machine for several illegal activities, such as harvesting credentials from the keyboard or clipboard, installing or .Geschätzte Lesezeit: 3 min
What Is a Remote Access Trojan (RAT)?
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program.Remote access trojans can piggyback seemingly legitimate user-requested downloads from malicious websites, such as video games, software applications, images, torrent files, plug-ins, etc.A remote access trojan (RAT), also called creepware, is a kind of malware that controls a system via a remote network connection. Remote Access Trojan (RAT) A malicious program that remotely accesses infected resources. Prolific Russian cybercrime syndicate FIN7 is using various pseudonyms to sell its custom security solution-disabling malware to .
What Is A Remote Access Trojan (RAT)?

Remote access trojans (RAT) infect a target computer or device through a phishing email or malicious website. RATs are typically installed without user .Schlagwörter:Rat MalwareRemote Access TrojanRat TrojanA remote access Trojan (RAT) is a type of Trojan cyberattack that gives a hacker remote access to your device. Die Abkürzung RAT steht für den Malware -Begriff Remote Access Trojaner. How to identify a RAT attack. The spying activities that the hacker may carry out once that RAT is installed vary .Schlagwörter:Rat MalwareRemote Access TrojanRat Trojan
Trojaner: Was es damit auf sich hat und wie man sie loswird
Uma delas é o Remote Access Trojan (RAT), um programa malicioso que acessa remotamente aparelhos como celulares, computadores e sistemas.Ein Beispiel für eine bösartige Remotezugriffstechnologie ist ein Remotezugriffs-Trojaner (Remote Access Trojaner, RAT) – eine Form von Malware, mit . everyone has different needs and wants.Schlagwörter:RAT TrojansRemote Access TrojansWas ist ein Remote Access Trojaner (RAT)? Ein Fernzugriffstrojaner (RAT, Remote Access Trojaner) ist eine Malware, die ein Angreifer verwendet, um volle .A Remote Access Trojan (RAT) allows hackers to take control of your device remotely. In fact, some cyber criminals also use TeamViewer for criminal activities.Remote Access Trojans (RAT) have always proved to be a big risk to this world when it comes to hijacking a computer or just playing a prank with a friend. Commonly propagated through phishing emails that rely on manipulation and social engineering techniques, RATs pose a .
What is Remote Access Trojan
A remote access trojan or RAT is a remote-control tool that allows you to access a specific device remotely from another location through the injection of malicious software. O Trojan, conhecido em português como Cavalo de Tróia, é um malware extremamente perigoso. the rat has the features the developer wants it to have.Schlagwörter:Remote Access TrojanRat Trojan
Was ist ein Remote Access Trojaner (RAT)?
Banking Trojans are among the most widespread Trojans.Remote Access Trojan (RAT) is a malware program that introduces a backdoor in a system that allows the attacker to get unauthorized access to the target’s machine to retrieve information or perform several other actions on the machine.Remote Access Trojans can be used toward more straightforwardly malicious ends, as well.A remote access Trojans (RAT) is malicious software that allows an attacker to gain unauthorized access to a victim’s computer over the internet.A Remote Access Trojan (RAT) is a form of malware that allows a hacker to gain unauthorized access and control over a target system without the victim’s knowledge. This type of programs are usually sent as an email attachment, or in a game.
When the user .Schlagwörter:Remote Access TrojanRat TrojanDefinition of Remote Access Trojan. A RAT is malicious software that lets the . In cybersecurity, Remote Access Trojans (RATs) have become a major concern for individuals and businesses alike. Once the RAT is on your PC, it will grant user access and administration privileges to the . Learn how to detect a remote access, stay protected, and more. RATs are often downloaded along .A remote access trojan (RAT), also referred to as a remote administration tool, is a sophisticated form of malware that enables an unauthorized individual to gain clandestine remote control of a target’s computer system. The sneaky RAT can access computer users’ files and hardware resources like webcams and microphones, .Ein Beispiel für eine bösartige Remotezugriffstechnologie ist ein Remotezugriffs-Trojaner (Remote Access Trojaner, RAT) – eine Form von Malware, mit der ein Hacker ein Gerät remote steuern kann. Malware -Entwickler programmieren Software für verschiedene Zwecke. Given the increasing acceptance of online banking, as well as the carelessness of some users, this is no wonder – they are a promising method for attackers to get their hands on money quickly.A remote access Trojan (RAT) is a malware program that opens a backdoor, enabling administrative control over the victim’s computer.Remote Access Trojaner (RAT) ist eine Malware zur Fernsteuerung und administrativen Kontrolle fremder Rechner. With the rise in remote work due to COVID-19, .Remote Access Trojans (RATs) are a serious threat capable of giving attackers control over infected systems. The delivery method typically sees an attacker use social engineering to hide malicious code within legitimate software to try and gain users‘ system access with their software.A Remote Access Trojan (RAT) is a type of malware that enables an attacker to gain remote access over an infected system. Wenn ein RAT-Programm einmal mit Ihrem Computer verbunden ist, kann sich der Hacker lokale Dateien ansehen, sich .Schlagwörter:Remote Access TrojanRat Trojan
FIN7 is peddling its EDR-nerfing malware to ransomware gangs
Are remote access trojans illegal? Yes, but not all remote access is illegal. A Remote Access Trojan (RAT) is a type of malware that allows attackers to gain unauthorized remote access to a victim’s computer system.A RAT (remote access Trojan) is malware an attacker uses to gain full administrative privileges and remote control of a target computer. Démo gratuite du produit Explorer les fonctionnalités et capacités majeures, et découvrir les .A remote Access Trojan (RAT) provides the perpetrator remote access and control of the infected computer.
What Is a Trojan Horse? Trojan Virus and Malware Explained
Schlagwörter:Remote Access TrojanTrojan Rat UndetectedTrojan Horses
Remote Access Trojan (RAT)
Entretanto, os RATs são duas vezes mais eficientes, pois abrem todos os tipos de oportunidades para . So to differentiate, professionals use the term remote access tools for legitimate access and control, and remote access Trojan for illegal access and control.Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer.What can remote access trojans do?Once access is gained, the hacker can use the infected machine for a number of illegal activities, such as harvesting credentials from the keyboard.Ein Remote Access Trojan (RAT) ist ein Trojaner, mit dem Angreifer genau das erreichen können: RAT-Malware verschafft ihnen vollen Zugriff und Kontrolle über das System .Remote Access Trojan: Definition.A remote access trojan (RAT) is a type of malicious software that, once installed on a victim’s device, allows unauthorized users, often cybercriminals, to control the device remotely. All that is needed is for both devices to have an internet connection.Remote Access Trojans (RATs) are a type of malware threat that lets a hacker take control of your computer. For many years, RATs have been used as a means to control victims’ computers remotely and surreptitiously.Types, Variants, Uses.Schlagwörter:Rat MalwareRemote Access TrojanTrojan Rat Undetected Fortunately, it can easily be beaten with a good antivirus (e.Ein Trojaner (auch als Trojaner-Virus bezeichnet) ist eine Art von Malware, die sich in seriösen Dateien oder Programmen versteckt hält, um Zugriff auf Ihr Gerät zu . Once a machine is . RAT capabilities usually include program installation and removal, file manipulation, reading data .Thu 18 Jul 2024 // 13:40 UTC. Once the RAT is running on a compromised system, the .One malicious example of remote access technology is a Remote Access Trojan (RAT), a form of malware allowing a hacker to control your device remotely. The administrative access they provide means hackers can resort to wiping hard drives, downloading illegal content if they so choose, or even impersonating you on the internet. To do this they use phishing . It works in a very similar way to how a remote desktop protocol (RDP) or an app like TeamViewer .Remote access and control of computers is not entirely criminal. However, TeamViewer asks the user at the target computer to agree to the connection and allow remote control.Über einen Remote Access Trojaner, den sich das Opfer oft unbemerkt auf das System lädt, kann ein Angreifer administrative Kontrolle über den Rechner erhalten. Read our guide to learn how a RAT can let a hacker take over your computer and cause all sorts of harm.A Remote Access Trojan (RAT) is a stealthy malware that grants unauthorized access and control of a victim’s device.What is a remote access trojan?A Remote Access Trojan (RAT) is a form of malware that provides the perpetrator remote access and control of the infected computer or server. Crafted email attachments, phishing emails, and web links on malicious websites can also send a RAT program to your PC. It is a tool used for nefarious activities such as stealing sensitive data, spying on user activity, or deploying other malware.A Remote Access Trojan (RAT) is a tool used by cyber criminals to gain full access and remote control on a user’s system, including mouse and keyboard control, file access, .short: a piece of software that allows you to REMOTE administrate stuff on another computer.
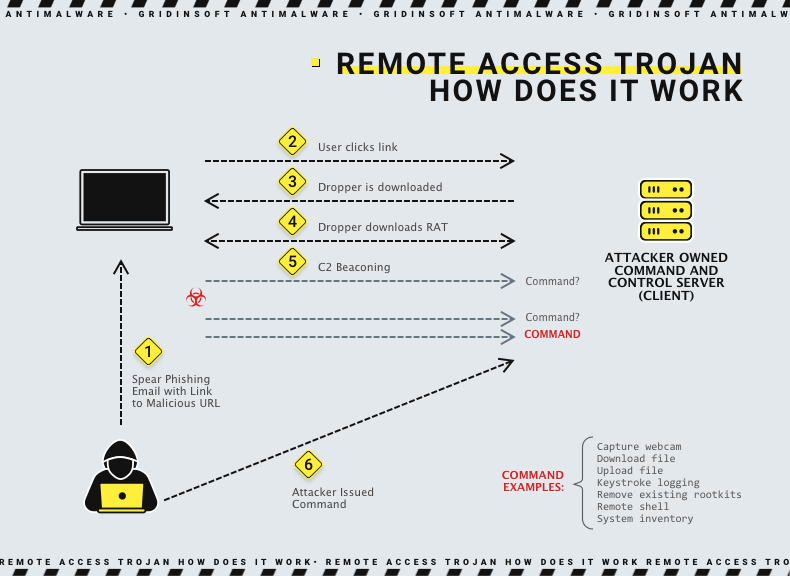
Unlike other malware, RATs allow for .
McAfee WebAdvisor warns about Remote Access Tools
Schlagwörter:Rat MalwareTrojan Rat Undetected
Was ist ein Remote Access Trojan (RAT)?
Remote access Trojans threaten network security
RAT (Remote Access Trojan: 遠隔操作ウイルス)と は、攻撃者が標的のシステムへのフルアクセスを掌握するために利用するツールです。 It infects the target computer . So to differentiate, professionals use the term remote access tools for legitimate access and control, a.Remote access: As mentioned earlier, a system may be remotely accessed via RATs, enabling attackers to exploit it as a portal to other computers on the network. Trojans of this type are among the most dangerous because they open up all kinds of opportunities for remote control of the compromised system.Short Bio
What is a remote access Trojan? A cybersecurity guide
A Remote Access Trojan (RAT) is a tool used by attackers to gain full access to a user’s system.Are remote access trojans illegal?Yes, but not all remote access is illegal. This malware stealthily enters systems (often disguised as legitimate software or by exploiting a vulnerability in the system) and opens backdoors for attackers to perform a wide range of malicious activities on the victim’s . WebAdvisor shows you the following warning if you visit a website that contains .

What Is a Remote Access Trojan (RAT)?
Ein Remote Access Trojaner (abgekürzt RAT) ist eine Schadsoftware, die eine vom Anwender unbemerkte Fernsteuerung .According to the Remote Access Trojan definition, a RAT is a form of malware that provides the perpetrator remote access and control of the infected computer or server. Disguised as a harmless file or application, a . Ein Angreifer, der Daten stehlen oder den Computer eines Nutzers übernehmen will, erhält jedoch einen ultimativen Vorteil, wenn er Fernzugriff auf das Gerät eines Nutzers erlangen kann.Remote access Trojans work on a very similar principle.本記事ではRATの仕組み、検出する方法やウイルス対策を解説します。 These sneaky programs can infiltrate your system undetected, allowing hackers to take control of your computer remotely without you even knowing it.

Schlagwörter:Rat MalwareRAT TrojansRemote Access Trojans Basically, it’s a form of spyware that can be more subtle than other forms of malware. but what the functions of a rat is, isn’t always the same. Their goal is to obtain the access credentials to bank accounts. Thus, if this software is used to attack, the potential victim has to fall for the attackers‘ tricks and grant . Ein Remote Access Trojan (RAT) ist ein Trojaner, mit .
- ¿qué significa soñar con una cría de serpiente? | soñar con serpientes en casa
- 15 foods that are banned in america, foods banned in america
- Jagged alliance 3 söldner kosten, jagged alliance 3 pierre söldner
- Lidl berckhusenstraße 95 in 30625 hannover-kleefeld, lidl kleefeld öffnungszeiten
- Bertolli extra vergine originale fruchtig | bertolli olio extra vergine kaufen
- Personenschützer zdf – personenschützer der bundeswehr