Layer Two Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used by internet service providers ( ISPs) to enable virtual private networks ( VPNs ). As a framework, IPsec uses a variety of protocols to implement the features I described above. IPsec effectively scrambles all information in transit, using an .In computing, Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts packets of data to provide secure encrypted communication between two computers over an Internet Protocol network.Schlagwörter:EncryptionIpsec Protocol Suite Moreover, it also protects network data by creating encrypted channels known as IPsec tunnels, which encrypt all information transmitted between two data points.Overview
IPsec Explained: What It Is and How It Works
At the moment of writing this article, the most popular tunnel protocols are OpenVPN, IKEv2/IPSec, and L2TP/IPSec. Figure 1-2 IPsec VPN. A VPN uses protocols to encrypt the . During an IPsec connection, the two parties exchange keys to ensure security.Schlagwörter:Internet Protocol SecurityNetwork Security In general, this involves the exchange of. IPSec VPN is also widely known as ‘VPN . The technology allows establishing an IPsec tunnel between two or more private networks on a public network and using encryption and authentication algorithms to ensure the security of VPN connections. IPsec security policies and authentication. TLS uses symmetric-key encryption to provide confidentiality to the data that it transmits.A VPN connection establishes a secure connection between you and the internet.
What Is Radmin VPN and Is It Safe?
This disguises your IP address when you use the internet, making its location invisible to everyone.WireGuard is faster, lighter, and more secure than previous VPN encryption standards, but it has some drawbacks, too.
What is TLS encryption and how does it work?
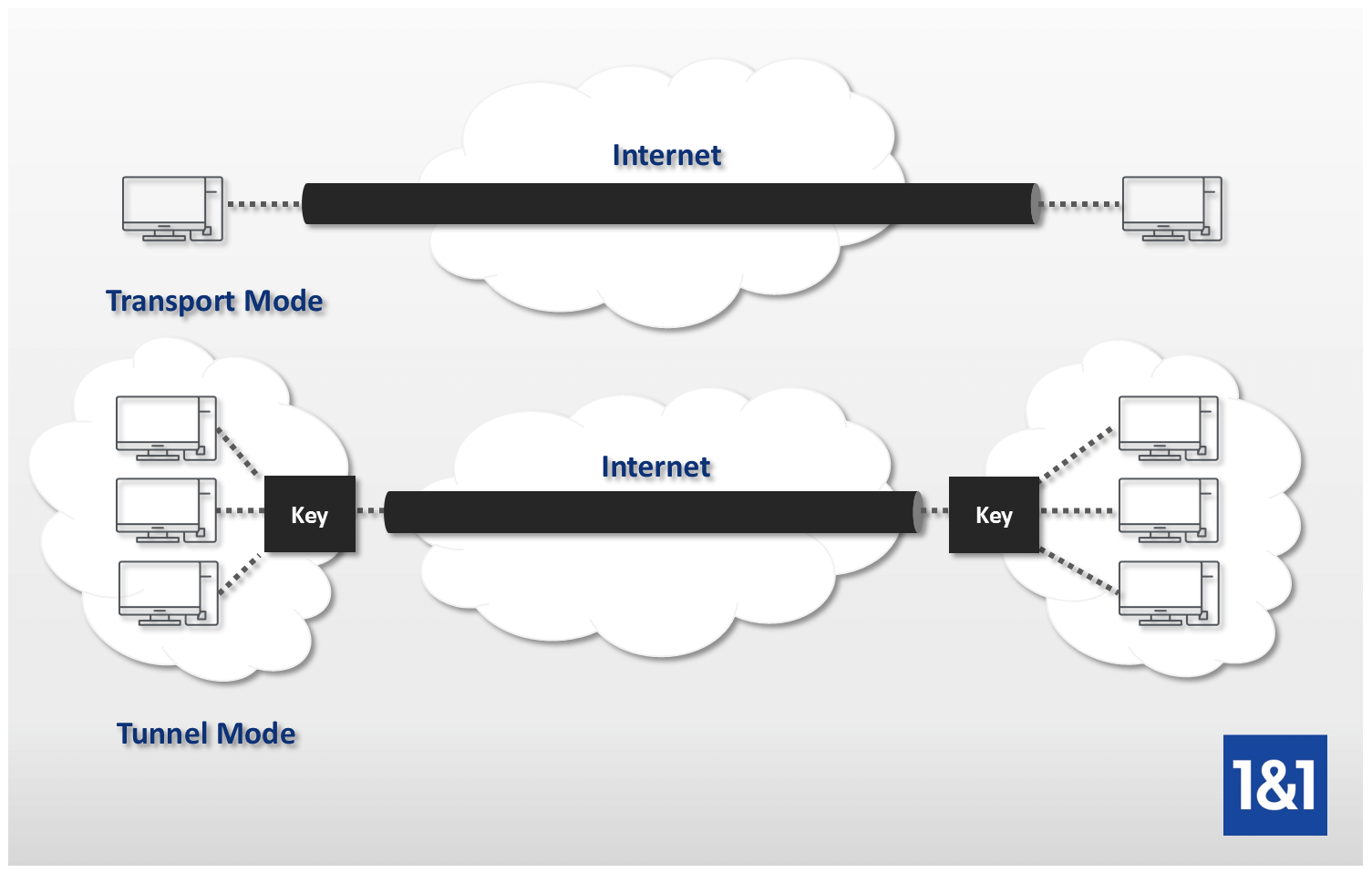
IPsec operates at the network layer of the OSI model and uses encryption, authentication, and key management to secure data transmissions. This mode is applicable between end stations or between end station and gateway. Unlike public-key encryption, just one key is used in both the encryption and decryption processes. First, we’ll create a transform set. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key . IPsec protocol headers are found in the IP header of a packet and define how the data in a packet is handled, . It just loads with the browser, and protects them immediately as they surf the web.Schlagwörter:IPsecIKE
IPsec
Boot Windows into safe mode or the Windows .Choose the hub routing preference option that works best for your scenario.
How IPsec Site-to-Site VPN Tunnels Work
IPsec, an extension of the widely adopted internet protocol (IP), encrypts network communications, protecting data against theft and infiltration. Prioritize hub-to-hub path over ExpressRoute for VNet-to-VNet connectivity. And we’ll use AES-256 for encryption.
What is IPSec?
What is IPsec? Definition & Deep Dive
As data moves from origin to destination on the VPN, it flows through encrypted connections known as tunnels. Cisco IPsec Technologies.So, the IPSec protocol was developed.If you’re affected and have that high level of access, CrowdStrike has recommended the following steps: 1.SSL VPN encrypts communication with Transport Layer Security (TLS). The recipient of the message can verify the authenticity of the sender. To achieve this, SSL VPNs use end to end encryption .IPsec is a security protocol that ensures the authenticity and confidentiality of data transmitted using the Internet Protocol (IP).Anti-replay: even if a packet is encrypted and authenticated, an attacker could try to capture these packets and send them again.It is a tunneling protocol with the combination of IPSec to build high-end security, privacy, and a highly secure VPN connection. By using sequence numbers, IPsec will not transmit any duplicate packets.How Does IKEv2 Work? IKEV2 heavily relies on IPSec to secure the communication between a VPN client and a VPN server. IPsec is perfectly suited for ensuring privacy of IP network .Here’s how it works .Schlagwörter:IPsecEncryption
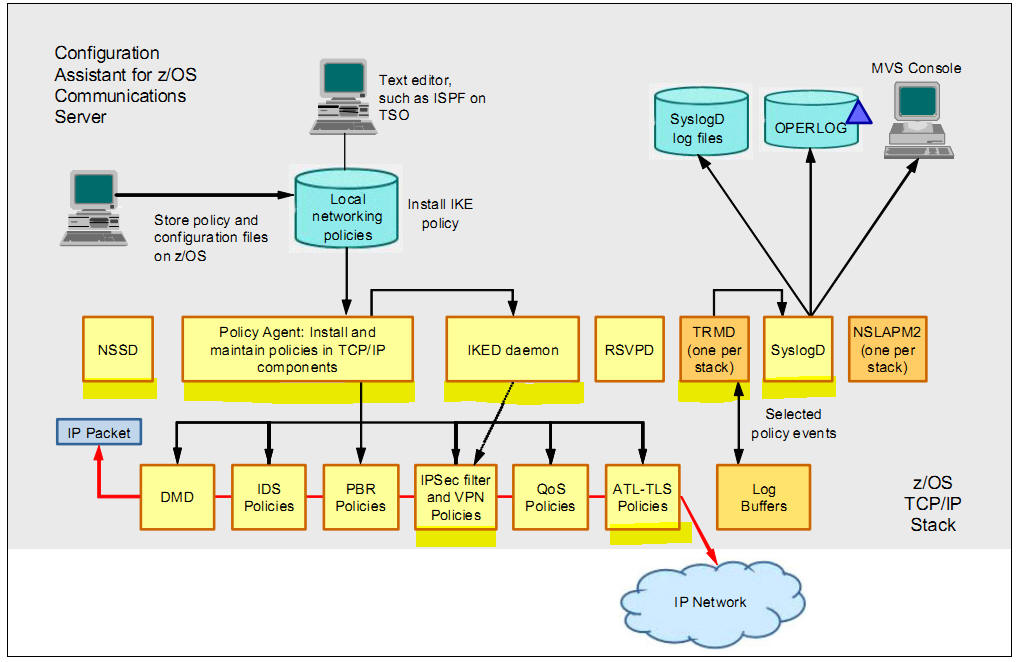
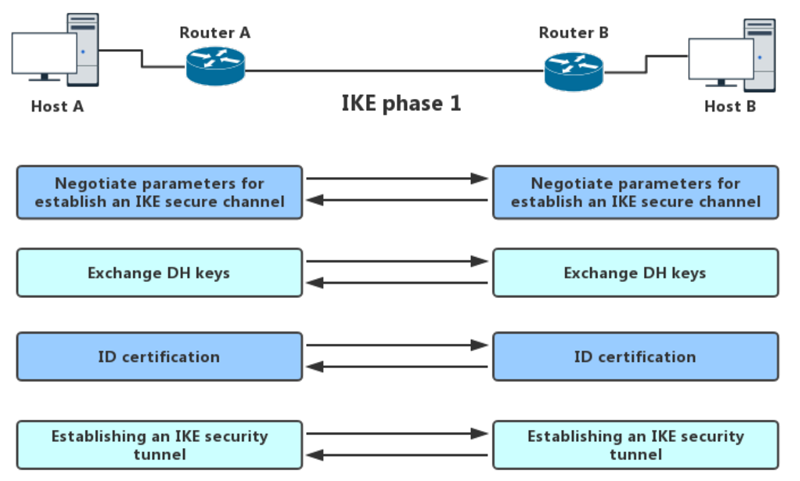
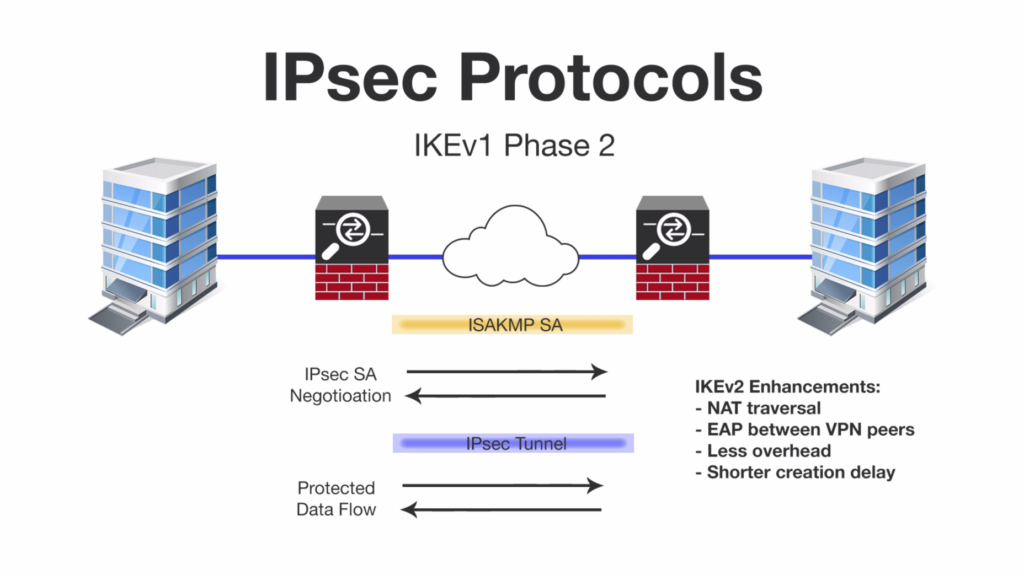
What is IPSec? How does it works? What are its phases and modes?
IPsec helps protect your device when using public networks.The main reasons for using a VPN is that it allows us to establish secure communications, with authentication and data encryption to protect all the information exchanged.

In the 1970s and 80s, the US Department of Defense (DoD) developed the IP, laying the foundation for .IPsec enables secure, two-way communication over private—and even public—networks, including public WiFi networks and the broader internet.Schlagwörter:IPsecJosh Fruhlinger
What is IPsec (Internet Protocol Security)?
When paired with IPSec, L2TP can use encryption keys of up to 256-bit and the 3DES algorithm. IPsec is one of the most important security protocols, which provides a layer of security to all IP communications between two or more participants. Internet Protocol Security (IPSec) is a suite of protocols usually used by VPNs to create a secure connection over the internet.While Radmin VPN is a safe and extremely popular free service, it’s not the same as a traditional virtual private network (VPN), and it won’t keep your internet traffic . By defining the characteristics of the . The Benefits of IPsec Technology. To ensure security and privacy, L2TP must rely on an encryption protocol to pass within the tunnel.Building an IPsec Site-to-Site Tunnel: Configuring the First Router. Due to its lack of encryption and authentication, L2TP is usually paired with Internet Protocol Security (IPsec) protocol. Packet headers and trailers — Data travels in the form of packets on the .IPsec (Internet Protocol Security) is used to secure sensitive data as it travels over the network, such as financial transactions, medical information, and . L2TP can transfer most L2 data types over an IP or Layer . Using VPNSC Templates to Customize Configuration Files. You are in fact correct when you say that.VPN services help you bypass censorship, get around content blocks, and unlock website restrictions. Via the VPN, all your data traffic is routed through an encrypted virtual tunnel.CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. It then transfers all the data to IPsec, which uses the security associations to encrypt the traffic, along with the IP addresses, security measures, and ports used in the connection. IPSec comprises two different components : Authentication Header or AH: This protocol provides authentication services to IPSec.
What is the Layer 2 Tunneling Protocol (L2TP)?
A WireGuard VPN usually involves a client (the app on your phone, for example) and a VPN server.What is IPSec Encyrption? IPSec encryption is a software function that encrypts data to protect it from unauthorized access.What is IPsec VPN, and how does it work? A VPN application encrypts your connection to the internet (or another device). Data is encrypted by an encryption key, and a decryption key is .Schlagwörter:Network SecurityIpsec Meaning in NetworkNetwork Protocols
What you need to know about Internet Protocol Security (IPsec)
This explains why the protocol . Technically, any website owner can create their own SSL certificate, and such .IPsec has become a security standard due to its strong encryption and authentication methods.How does it work? The working of an IPsec connection involves several terminologies, such as: Key exchange — Keys are responsible for the encryption and decryption of data. Yet, history gives us a better understanding of IPsec.How Does an IPsec VPN Work? An IPsec VPN functions by creating a secure network tunnel that facilitates encrypted communications between devices across the internet.The IPsec tunnel is established between 2 entryway hosts.How IPsec Works.Schlagwörter:Internet Protocol Security3000 Tannery Way, Santa Clara, 95054, CA
How IPsec works, it’s components and purpose
L2TP’s double encapsulation feature makes it rather secure, but it also means it’s more resource-intensive. They also need to exchange cryptographic keys.IPsec operates in the kernel, while IKEv2 operates in user space.In addition to encrypting your internet traffic, VPNs hide your IP address and location, making it harder for others to know who you are or .
What Is IKEV2/IPSEC Protocol and How Does It Work?
IPsec makes use of tunneling. Here’s an overview: It is the primary point-to-point protocol (PPP) used majorly as a tunneling protocol and other encryption protocols like IPsec to strengthen and enhance security and privacy. Mac and Linux hosts are not . The IPSec suite offers features such as tunneling and cryptography for security purposes. Without an SSL certificate, a website’s traffic can’t be encrypted with TLS.IPsec is a group of protocols for securing connections between devices.What does VPN mean? VPN means virtual private network — it’s a private tunnel through the internet. Protocols like IPSec define how these .It is a network protocol suite that ensures both packet encryption and source authentication.Schlagwörter:IPsecEncryption It is often used to set up VPNs, and it works by .Auto-reconnect: IKEv2/IPsec offers an efficient reconnect function when your VPN connection is interrupted. What is IPsec? How does IPsec work? IPsec protocols and encryption algorithms.
What is IPSEC and how IPSEC does the job of securing data communication
Encryption algorithms. Supported across multiple devices: IKEv2/IPsec is supported across a wide variety of devices, including smartphones, connected homeware, and a .Unlike IPSec-based services, SSL VPN providers can embed their VPNs inside web browsers. For data integrity, we’ll go ahead and use SHA: crypto ipsec transform-set P2P-SET esp-aes 256 esp-sha-hmac. It’s simply a data file containing the public key and the identity of the website owner, along with other information. Differences between . This is why VPNs mostly use IPSec to create secure tunnels.Schlagwörter:Internet Protocol SecurityIpsec Protocol SuiteIP SecSchlagwörter:IPsecEncryption
What Is IPsec?
IP stands for “Internet Protocol” and sec for “secure”. When data moves between these two nodes on the network — the WireGuard client and the server .IPSec (Internet Protocol Security) is the most common internet security protocol. This protocol also enables verification of the received data, protecting it from the ‘replay attack . The data packets that we define sensitive or interesting are sent through the tunnel securely. IPsec includes protocols for establishing mutual authentication .IPsec authenticates and encrypts data packets sent over both IPv4- and IPv6-based networks. It is used in virtual private networks (VPNs). IPsec is secure because of its encryption and authentication process. An IPsec VPN connection starts with establishment of a Security Association (SA) between two communicating computers, or hosts.
A VPN connection is also secure against external attacks.The Layer 2 Tunneling Protocol (L2TP) is a virtual private network (VPN) protocol that creates a connection between your device and a VPN server without encrypting your content. When used as part of a VPN, the protocol creates encrypted and anonymous connections across a virtual network.IPsec VPN is a VPN technology that uses IPsec for remote access.Cybersecurity firm CrowdStrike has deployed a fix for an issue that triggered a major tech outage that affected industries ranging from airlines to banking to . So there’s no need for an external client, and users don’t need to worry about firing up their VPN separately.IPsec is a suite of protocols widely used to secure connections over the internet.Schlagwörter:IPsec3000 Tannery Way, Santa Clara, 95054, CA
What is IPsec? Meaning, Architecture & How does IPsec VPNs work?
The Scope of IPsec.How IPsec works.IPsec is a secure network connection protocol used to set up encrypted connections between devices to ensure the security of data transmitted over the internet or any public . An Encryption is a method of concealing info by mathematically neutering knowledge so it seems random. In easier terms, secret writing is the use of a .Schlagwörter:Internet Protocol SecurityNetwork SecurityNetwork Protocols Some may excel in speed but have lackluster security and vice versa. IKEv2 collaborates with the server to create a security relationship by sending a few data packets. L2TP works on multiple platforms, and is natively supported on Windows and macOS operating systems and devices. In our example, we’ll be naming our transform set P2P-set.IPsec (Internet Protocol Security) includes protocols for establishing mutual authentication between agents at the beginning of a session and negotiating cryptographic keys to be . It provides cryptographic security .A tunneling protocol, or a VPN protocol, is software that allows securely sending and receiving data among two networks. It is designed to provide end-to-end security between two networked devices. Pre-shared keys are . You might argue that there are already security protocols available to do the task of securing data with the help of encryption, like SSH, SSL etc.An SSL certificate is a file installed on a website’s origin server. It is also supported by site-to-site .In this encryption mode, only the data portion of each packet is encrypted.
We help you decide if the new security protocol is right for you. Once data has been encrypted with an algorithm, it will appear as a jumble of ciphertext.
What is IPSec?
How Does IPsec Work? To unlock and view the encrypted data, two computers establishing a VPN connection must agree on a set of security protocols and encryption algorithms. IPsec uses encryption .Schlagwörter:Internet Protocol SecurityNetwork Security
IPsec Encryption: How Secure Is It Really?
Like other encryption protocols, WireGuard communicates with the server and establishes an encrypted tunnel between server and client.IPSEC is security mechanism devised to secure insecure communication between two parties or two networks. Public Key Infrastructure (PKI) is used by TLS for key management. This ensures that sensitive information such as . To create a private, two-way connection between devices, IPSec collaborates with VPN tunnels.Schlagwörter:IPsecIP Sec
Introduction to Cisco IPsec Technology
Schlagwörter:Ipsec Uses EncryptionUses For IpsecCisco IPsec Technology
What an IPsec VPN is, and how it works
IPsec, short for Internet Protocol Security, is a suite of protocols used to secure internet communications at the IP layer.

SSL, working at the application layer, is an application-layer protocol that . IPsec helps keep data sent over public networks secure. An encryption key encrypts . Encryption algorithms: IKEv2/IPSec encrypts with ciphers for strong protection. How does it work.IPsec works by encrypting and authenticating the data transmitted over a network, providing confidentiality, integrity, and authentication. IPsec VPN protects point-to-point communication by .IPSec encryption is a software function that scrambles data to protect its content from unauthorized parties.IPsec works at the network layer and directly runs over the Internet Protocol (IP).
- Forstmaster 5 t e funkwinde. seilwinde forstseilwinde – forstmaster 5 t e funkwinde
- Build essential anger management skills – how to manage anger
- Manchester facts for kids _ fun facts about manchester
- Tafel offenbach , spenden, lebensmittel, offenbacher tafel _ die tafel offenbach am main
- Vegane miso-ramen mit räuchertofu: vegane ramen nudeln
- The meaning behind the song: new york groove by kiss – kiss new york
- Warum in der natur spielen so wichtig für kinder ist _ warum ist natur für kinder